As things stand today, I have a site-to-site VPN between on-prem and Azure which works well.
I am currently using an SSL VPN to my on-prem, but would like to migrate my clients to all use Point-to-Site VPN in Azure since we're moving all of our key infrastructure there. In my perfect future case, Azure is the core of everything, and my local on-prem is just a glorified hotspot where my users don't have to VPN from and it's faster.
I can ping back and forth from Azure to On-Prem, and my SSL VPN clients can ping into either Azure or On-Prem subnets with no problem. However, when my clients connect to Point-to-Site in Azure, they can ping VMs running in Azure, but they can't reach any systems on my local On-Prem network. This will cause challenges for the migration because it means I basically have to "big-bang" the cutover rather than moving things as it makes sense.
Here's the setup:
Local Site - 10.0.20.0/24 < ---- Site to Site VPN ----> Azure Site - 10.0.40.0/24
| |
| |
| |
Local VPN Client - 10.0.30.0/24 Azure Point-to-Site VPN - 10.0.50.0/24
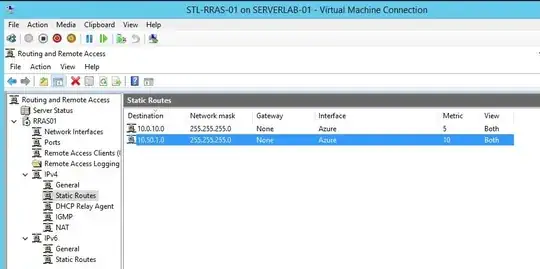
Basically, trying to understand what I might be missing that would prevent clients on Point-to-Site from getting back to the local Site. I've checked firewall rules on the local site side, but the packets don't ever seem to even be showing up there in a packet dump.
Of interest, my best guess at this point after troubleshooting is that the IKEv2 Proposals list 10.0.20.0 <-> 10.0.40.0 and 10.0.30.0 <-> 10.0.40.0, but there's no way to get a tunnel for 10.0.20.0 <-> 10.0.50.0 to come up since Azure auto brings it up based on the subnet configuration and I can't seem to make the Point-To-Site subnet part of a subnet I've defined as part of the VNet connection. I'm wondering if that means Azure wont route from the P2S subnet back to the local site since it doesn't match a Phase 2 proposal, and if so, is there any way to make the Azure side add it so I can bring that up as part of the tunnel.
Any help is appreciated