I have a site-to-site VPN setup with StrongSwan between AWS and Azure. In AWS we use Route53 in our VPC to map something like production-db.internal.com to the the AWS-provided name for our RDS cluster. How can I set up my DNS servers for the Azure Virtual Network to able to resolve production-db.internal.com to the local ip address of the RDS instance in the AWS VPC?
2 Answers
In AWS, you can to use a Simple AD to expose the private DNS server across the VPN. You can then configure the IP of that Simple AD server as the DNS server for the Azure virtual network.
- 336
- 1
- 7
I'm not familiar with the Route53, if it has a private or public IP address, then you just need to configure the Azure VNet to use it as DNS service. If it has a private IP address, please make sure that the VMs on Azure are able to reach it through your S2S VPN.
If it doesn't expose its' IP address, then you just need to build your own DNS server. Windows Server or Linux BIND, there are several solutions to achieve your goal.
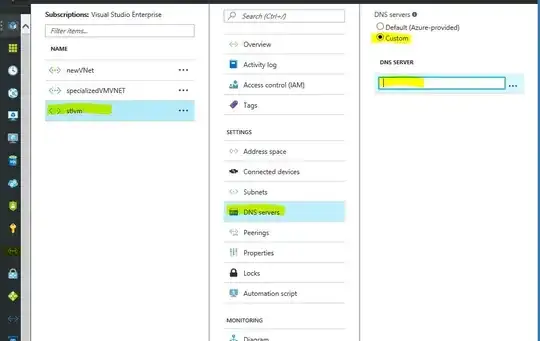
To add the custom DNS settings, please refer to the screenshot below:
Note: We need to reboot the VM to make them get the new DNS settings.
- 713
- 4
- 8
-
I ended up using BIND9 on an Ubuntu server in the AWS VPC and added its private IP to DNS server list in the Azure VNet. Seems to be doing the job – MarkAWard Nov 04 '16 at 20:24