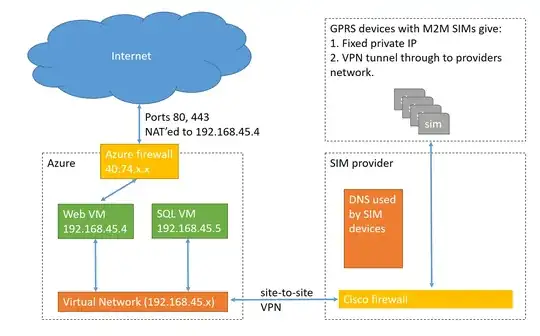
I've setup a virtual network in Azure with a site-to-site VPN tunnel. So far so good, but the tunneled devices cannot access my servies via the public IP, they can only access via the local IP. Seems something prevents VPN devices to access the public IP of a VM connected to the same virtual network.
So say api.mydomain.com is mapped via DNS to the public IP of a VM. That works fine for all internet devices, but not the ones that goes though the site-to-site VPN tunnel. They can access fine via the local ip (192.168.x.x) though.
Any way I can open access/route the traffic coming in via the site-to-site VPN to the public IP address? The devices in question are GPRS devices and uses the DNS of the cell operator. So nothing much I can do there (like adding an entry to point to the local address).