I installed a Comodo Certificate on Windows Server 2012 / IIS 8.5. For most clients this certificate works without a hitch, but older Android units running Chrome and also Chrome on MacOS Sierra cannot access the site properly because the site is marked as untrusted.
When running SSL Test from SSL labs i get this result:
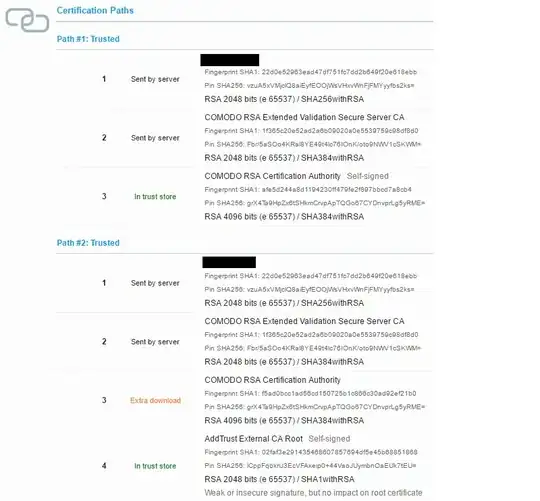
Basically there are two certification paths where one is requiring extra download.
The only solution provided by the vendor of the certificate is to disable all uses of the "COMODO RSA Certification Authority", however this will only work until the next update of the trusted root certification list and requires a reboot each time.
Should I get a certificate from another vendor (seems easier?) or is it possible to extract parts from the issued certificate and rebuild a proper chain?