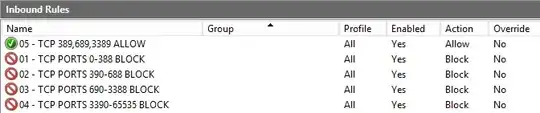
The Windows Firewall does not react as a standard network Firewall.
When you have more than one rule matching your traffic, then the Block one will have precedence, regardless the rules order.
If you have rules with both Allow and Block that will match traffic, then it will Blocked.
As a consequence, the following rules you are probably trying to set WILL NOT WORK, as the block rules for all udp/tcp ports will take precedence over the allowed ones for RDP/LDAP :
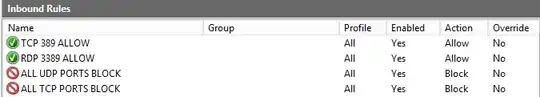
So, what to do now from there ?
1) Check-out the "Override" column.
There it's setup to "No". You can setup it to "yes" but then you will need to specify an allowed computer or computer group...depending on your context (e.g AD or not) this option could not apply to you :
Use this option to allow the connections that match this firewall rule
to override any firewall rules that explicitly block connections. This
option is also known as authenticated bypass. Normally, rules that
explicitly block connections have priority over rules that allow
connections. If you use this option, the connection is allowed even if
another rule blocks the connection. This option is most often used for
vulnerability scanners. If you do not use this option, any blocking
firewall rules that match the same firewall rule criteria will take
precedence and the connections will be blocked. If you select this
option, you must specify at least one computer or computer group for
authorization on the Users and Computers tab.
https://technet.microsoft.com/en-us/library/cc730690(v=ws.10).aspx
2) Explicitly deny ports that overlap ones you explicitely need to allow, then allow only ones you need to open :