I was wondering if anyone could give some background on differentiating between a server firewall and AWS Security Groups?
4 Answers
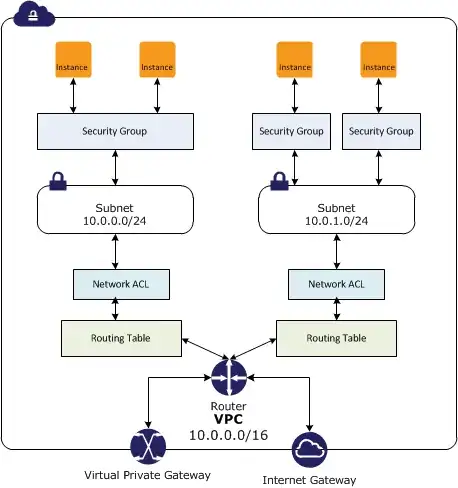
Security groups are stateful, in that reply traffic is automatically allowed. A security group can be applied to many instances. Once applied the rules can be changed on the fly, but you can't change the group that an instance is in. Security groups are enforced at the hypervisor level.
Network ACLs are stateless, in that you have to specify rules for each direction. A NACL applies to one or more subnets. The rules can be changed on the fly. NACLs are applied at the network level. You have to explicitly add higher ports to allow for replies in some cases - see here.
Software firewalls running on an instance run within the OS, and so take up your CPU cycles. Personally I don't use these within AWS as the provided features are more than adequate.
Traditional hardware firewalls can't be used in AWS, but the equivalent is the NACL.
I primarily use security groups, as they're easiest to use. If you have a lot of extra traffic hitting your instance you could in theory reduce the work the machine is doing by adding NACLs. Using both is overkill, but doesn't hurt, and may slightly increase your security.
- 31,888
- 7
- 52
- 78
-
Network ACLs are stateless please fix your post thanks – ob_dev May 25 '17 at 18:42
-
@obo thanks for the correction. The word was incorrect, but the explanation after it was right. I'll review the whole answer. – Tim May 25 '17 at 20:15
A security group acts as a virtual firewall that controls the traffic for one or more instances. When you launch an instance, you associate one or more security groups with the instance. You add rules to each security group that allow traffic to or from its associated instances. You can modify the rules for a security group at any time; the new rules are automatically applied to all instances that are associated with the security group.
A server Firewall is usually a system designed to prevent unauthorized access to or from a private network. You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets.
Groups are mainly different because say if you have Server A,B,C,D you can make a group that will allow server A + B + C to all talk to each other but D cant. You can have all of the server behind the same "FIREWALL" which is usually Global to everything in the network.
- 111
- 3
A security group it can be applied to a number of servers. The syntax is similar to a firewall however you can as well apply source/destination from a different security group. So in that sense is more like a template.
However security groups apply only for inbound traffic as a server firewall like iptables that allows a lot more configurations for inboud, outbound, nat etc.
When you should use or an other ?! It depends by your requirements for basic firewall you can use the security groups in AWS for more complicated scenarios local firewall is more appropriate since you have a lot more options.
In practice for a decent security site you may use both though increases complexity.
- 2,687
- 2
- 18
- 19
The software firewall also suffers in that if the server is compromised, the firewall is too, though I usually am more interested in incoming than outgoing traffic.
In enterprises: Software firewall administered by the server admins. Aws (or hardware in a private cloud) would be handled by the networking administrator or security team.
- 1