The problem: I can't give a computer account the permissions to add groups to an OU by adding that computer account to a security group that has been granted the permission to add groups to that OU.
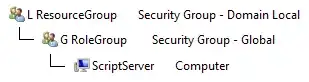
The reason: In our environment resources are always presented to users using role groups. The resource here is the permission on a specific OU which is given to a Domain Local security group. The role is a Global security group and the user is a computer account. The reason the user is a computer account is because the script that requires the permissions is running under the SYSTEM account on that server.
The set-up:
What I already tested:
- If I delegate the permissions directly to the computer account it works.
- If I put a user in the role group that user can execute the script.
What I want:
- A solution to make this setup work (maybe I overlooked something)
- Or an explanation why this won't work (then I'll try to find an other solution)