Last evening my forum was victim of a DDOS Attack in the form of a DDOS Attack. I've confirmed it was an HTTP Flood.
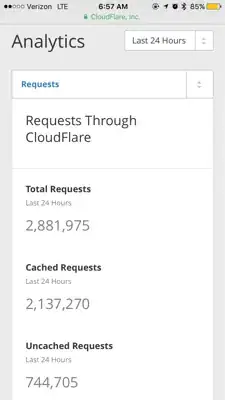 The first thing I did was enable CloudFlare's checking your browser. It blocked a large amount of requests and apache started responding again.
The first thing I did was enable CloudFlare's checking your browser. It blocked a large amount of requests and apache started responding again.
Next I got a message on MyBB saying too many MySQL connections were open. So I stoped apache and MySQL.
I proceeded to lift the connection limits to 10,000 whether my webserver is able to handle things is another question but the limits would no longer cause an error.
Next I started MySQL then apache. The Attack only had 200 connections at this point due to the whole checking your browser thing.
Afterwards I adjusted my firewall settings at AWS to only allow connections from CloudFlare IP Ranges. And saved the settings
At this point the site was back up. Am I missing any steps. How can I stop HTTP flood attacks in the future?