We are a small business and have been successfully running one Hyper-V 2012 R2 vmhost with many Windows Server 2012 VMS that includes a DC, Web Server, CRM Server and SQL Server for a couple of years. For networking we have a Draytek 2860, 2 physical switches and a gigawan.
We don't have an IT Department - yet - and I'm primarily a coder, but I do dab on systems and networking (I planned and did the setup above) but do not have enough know-how to confirm my R&D, so thank you serverfault for existing :)
As we've grown so did our traffic and I'm now finding that during business hours the network performance is being affected by all sorts of traffic, internal and external.
So, this weekend I embarked on a journey to improve the networks reliability and also deploy a DMZ Zone for staging and testing accessible via the internet.
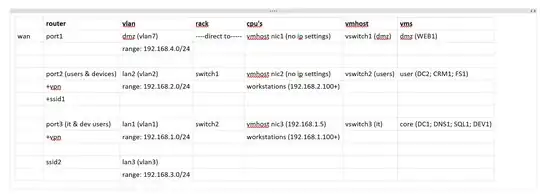
So after much reading about the Router (Draytek 2860), Hyper-V networking and Vlans I've come up with the following setup, that I'm hopeful of integrating successfully today, before everyone's back in the office tomorrow:
'Read from left to right, as if there is a link between columns in the same row.
Please note that:
- I want the servers on the DMZ to be domain controlled and have access to some IT servers, like the SQL Server.
- All subnets/vlans will share the same DNS server on the "it & dev" vlan, secondary will be the router, e.g. 191.168.1.1
- DMZ subnet/vlan only has access to "it & dev" vlan
- Lan3 is for guests that connect to a separate wireless SSID on the router but should have access to the DMZ subnet, e.g. client that comes in for project demo.
- My VMHost does have 3 physical NIC's - thinking ahead to this purchase ;)
So the questions/clarifications I'm looking for are:
- Is separating user traffic from "it & dev" and "user & devices" traffic into a vlan each a sensible approach to improve performance? It makes sense to me, but just looking for confirmation.
- This routher has inter-lan routing, that from what I can understand is a NAT feature to have inter-lan/vlans routing. But would I still need to use static routes, or the Inter-Lan Routing will suffice for regular traffic?
- I currently only have one DC1, but am thinking about deploying a second one, do you think it’s a good idea for one to be on the "user & devices" vlan and another on the "it & dev" vlan, or should they always be on the same vlan? Bear in mind that the DMZ will not have access to the "user & devices vlan", only the "it & dev" one. Will it be bad if a server on the DMZ cannot find the secondary DC, because that's on the "user & devices vlan"?
- I'm not considering storage uyt (SAN’s or something similar yet) but am seriously considering for the File Server, VM’s and internal backups, could you point me in the right direction for a sensible (cost and setup) solution?
- I'm also thinking about having another physical vmhost, should I separate the vms per vlan? For example having a vmhost for the user vms and another vmhost for the dev and dmz vms?
- If there's anything, drawback, pitfalls or things I should be aware of whilst implementing this please do let me know.