Turns out the issue relates to installing a SHA-2 certificate. If anyone else is experiencing the same problem post a comment I and can run through the entire procedure :-)
As requested here is the full procedure, with special thanks to IBM support :-)
Here is the link to IBM http://www-01.ibm.com/support/docview.wss?uid=swg21268695
To implement the SHA-2 certificate on your Domino server you must have these pre-requisites first.
1: Download and install the KYRTool on the same Domino Administrator client referenced in step 1 by placing the W32 kyrtool.exe in the Notes program directory. Refer to the wiki articles linked below for instructions on installing and running KYRTool. KYRTool is capable of handling SHA-2 certificates.
KYRTool
Download link: http://www-933.ibm.com/support/fixcentral/swg/selectFixes?parent=ibm~Lotus&product=ibm/Lotus/Lotus+Domino&release=9.0.1.2&platform=All&function=fixId&fixids=KYRTool_9x_ClientServer
Place the KYRTool in the Notes program directory, as it relies on .DLLs installed by Notes.
If you have the Notes/Domino program directory in your system's PATH environment variable, this can be installed to any directory.
2: Before you begin, note the following information about running KYRTool & OpenSSL
If you have a command line parameter with spaces in it, such as the path to a file, the space can cause the command line to be read incorrectly, resulting in errors. This can affect running commands for both OpenSSL and KYRTool
To include a space in a parameter, the parameter must be delimited with quotation marks. For example, if Notes were installed in the Program Files directory, then the command line for creating a keyring might look like this:
kyrtool ="c:\Program Files\IBM\Notes\notes.ini" create -k "c:\Program Files\IBM\Notes\data\keyring.kyr" -p password
3: OpenSSL
Download links for the Windows versions of OpenSSL are available at https://slproweb.com/products/Win32OpenSSL.html
The light version of OpenSSL is sufficient for the tasks required for creating a SHA-2 certificate. v1.0.2k is the latest recommended release as of today. Either the 32-bit or 64-bit version can be used if you are on Windows 7.
OpenSSL may need updates to Windows Visual C++ libraries. If the libraries are not up to date, a prompt will display during the OpenSSL install noting that updated Visual C++ libraries are needed. Links for downloading these libraries are also on the download page for OpenSSL.
A configuration file "openssl.cfg" will be extracted by the installer to the bin directory. In order for OpenSSL to read this configuration file, you must set an environment variable by running the following command from a DOS prompt
SET OPENSSL_CONF=\openssl.cfg
e.g. SET OPENSSL_CONF=c:\OpenSSL-Win64\bin\openssl.cfg
You run OpenSSL from the "openssl.exe" file, which is found in the \bin directory of the OpenSSL install. Open a command prompt window in this directory to run it. If you double click on openssl.exe, it will open in a DOS command window. If you launch OpenSSL this way, you enter only the name of the OpenSSL function in the command window. For example, instead of typing "openssl genrsa..." you would enter "genrsa..."
When you have everything ready, next step is to follow the instructions for generating the CSR and the kyring file.
(Steps 1 to 6 should be done on any workstation machine that has Administrator client, OpenSSL tool installed)
Here are the steps for setting up SSL with SHA-2 certs:
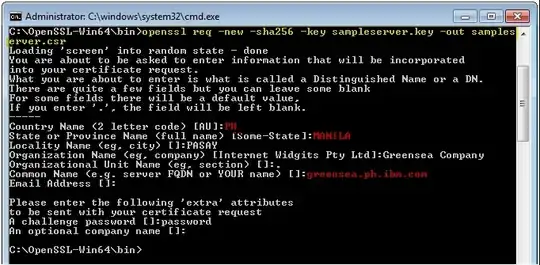
Step 1: Open Command Prompt and point to the path where the OpenSSL is located and input the command
" openssl genrsa -out server.key 4096 "
This will generate whatever name of RSA key you typed in (from my example it will create a "sampleserver.key" on c:\Openssl-win64\bin). You should keep this because you will later need this file when your on the merging the certificate on the keyfile. This contains private key.

Step 2: Generate a Certificate Signing Request (CSR)
- Enter Common Name, State, Country
- Create using SHA-2
- You should be consistent with the name of your RSA key (the one that we generated in step 1) and the name of the CSR file (from my example I also used "sampleserver" as my CSR name just put ".csr",) This command will generate your CSR file and this file is the one that you will send to your CA provided so they could request for a certificate.
There is a method outlined here
http://www-10.lotus.com/ldd/ndseforum.nsf/xpTopicThread.xsp?documentId=ECCC40A836DA3C1885257D99004BF9B0
but for me it didn't work - created the ring key and when tested it came back with the certificate details, but failed when deployed.. this is a little longer but it does work
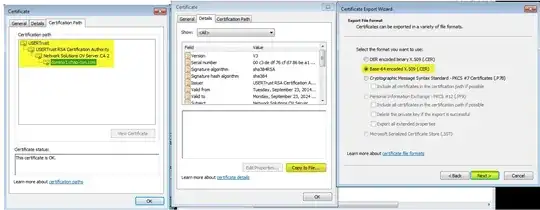
Step 3: Acquire an SSL/TLS certificate from a third party CA. When you received it make sure that certificates they provided you contains a root certificate (above the chain), intermediate certificate (second chain) and the site certificate (bottom of the chain, usually named as the fqdn you used when you created your CSR). On the screenshot below,
User trust is the root cert
USER trust RSA Certificate authority and Network Solutions OV Server CA 2 are the intermediate certs
and domino1.chap-con.com is the site cert
If would be convenient if you can extract it like we did.
Point to the certificate that you want to extract -> click "view certificate" -> go to "details tab".
it will open a new krypto shell window. Go to the "details" tab of that cert and click "copy to file button" and use BASE 64.
Then save it.
Step 4: We have to create the keyfile on the kyrtool. Open your Command Prompt and go to the path where your KYRTOOL is located. Create the keyfile by the command I've highlighted.

Step 5: Once you have all the certificate extracted, we will do the merging. Below is the correct order to follow when merging the certificate using the kyrtool.
IMPORT ROOTS
c:\Lotus\Notes>kyrtool import roots -i "C:\Path\root.crt" -k "C:\Path\keyring.kyr"
Using keyring path 'C:\Path\keyring.kyr'
SEC_mpfct_ImportTrustRootToKYR succeeded
c:\Lotus\Notes>kyrtool import roots -i "C:\Path\intermediate1.crt" -k "C:\Path\keyring.kyr"
Using keyring path 'C:\Path\keyring.kyr'
SEC_mpfct_ImportTrustRootToKYR succeeded
if there are 2 intermediate certs merge it also by the command above, just indicate the name of the second intermediate cert.
IMPORT KEY (RSA KEY GENERATED ON OPENSSL STEP 1)
c:\Lotus\Notes>kyrtool import keys -i "C:\Path\sampleserver.key" -k "C:\Path\keyring.kyr"
Using keyring path 'C:\Path\keyring.kyr'
Successfully read 4096 bit RSA private key SECIssUpdateKeyringPrivateKey succeeded
IMPORT SITE CERTIFICATE
c:\Lotus\Notes>kyrtool import certs -i "C:\Path\sitecertificate.crt" -k "C:\Path\keyring.kyr"
Using keyring path 'C:\Path\keyring.kyr'
SEC_mpfct_ImportTrustRootToKYR succeeded
Step 6: If the merging is successful copy the keyring.kyr and keyring.sth to the Domino DATA directory.
Step 7: Go to your server config and update the SSL keyfile name. On you Server document If you have "Load Internet configurations from server/internet sites documents" go to the "Web" tab -> Internet sites and open the Web site that you want to modify and open it
I also had to replace the name of the key ring at
Configuration > Server > Current Server Document > Ports > Internet Ports
When you have updated the records
tell http restart
You can test the mail server at
https://www.htbridge.com/ssl/
Just enter the domain name and port, you should get a result like this