I have a pretty straight forward setup: IIS 8 on Windows Server 2012 R2 2x ARR servers with NLB 3x Web content servers in a web farm
ARR servers have IIS shared configuration and IIS web content servers have shared configuration. I am able to sucessfully browse to a domain pointed to my ARR NLB IP over HTTP and hit my web servers in the web farm.
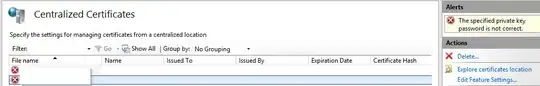
My problem is when I add certificates to the CCS share, they show up with a red X and the error "the specified private key password is not correct.". I have no key password specified in the CCS feature settings, and I generated a CSR and key without encryption to issue these test certificates from a valid CA.
The CSR and key's are all generated through a custom internal SSL utility which is just using OpenSSL. I ran the certificate and key through some validation tools on sslshopper.com and they verified to match and the key was able to be read as it was not encrypted.
I generated the PKCS#12 (.pfx) file using OpenSSL with my un-encrypted key and certificate issued from my CA. I am able to import the generated PFX into my cert store on my local machine, view it, and export it all without issue. Once strange thing I noticed is that when I exported the cert with key from my personal cert store on my machine and added it to the CCS, the error was that the file system could not find the file specified, even though it's displaying the cert with an error which is located in the share.
Any assistance would be greatly appreciated.