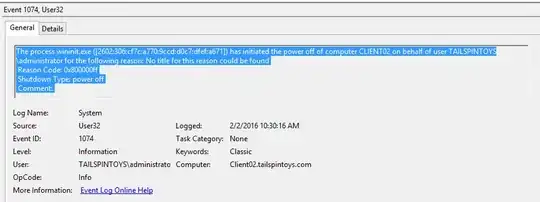
Converting my comments/thoughts into an answer.
It appears that you have given all of the students:
- Administrative control over all the computers.
- Anonymity by allowing them to all share the same admin account.
This is probably a suboptimal configuration in a typical classroom setting.
Although you claim that the students are not administrators on the computers, by default, only the Administrators group has the right to force the shutdown of a computer from a remote system. Check the User Rights Assignment category in your applicable local security policy or Group Policy:
Now, to more directly answer your question, there is probably not enough forensic evidence left on the computer right now to determine what computer the shutdown command was issued from. It is possible to enable more logging that would allow you to capture these events in the future, but enabling such logging now won't help you find out what happened in the past. Specifically, the logging that I'm thinking of that would have helped you is in the Advanced Audit Policy section (these are just examples, not an exhaustive list)
- Audit RPC Events
- Audit Filtering Platform Connections (Windows Firewall)
Remote shutdown uses RPC, so that's sure to show something. And logging when Windows Firewall permits an inbound connection will absolutely give you an IP address. You would be able to correlate the events.
Here's a step-by-step guide on configuring Advanced Audit Policy:
https://technet.microsoft.com/en-us/library/dd408940%28v=ws.10%29.aspx?f=255&MSPPError=-2147217396
Edit: Updating to confirm that as of Windows 8.1, the event log actually DOES include the IP address of the remote system that initiated the shutdown. (By default, without having to enable any additional logging.) But I do not know whether older versions of Windows include the IP address or not.