We have two of our sites connected via an MPLS that bypasses our firewall. Traffic between the sites, when hitting our core switch is routed directly to a second interface on our ISP's router.
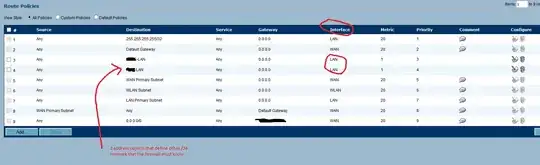
The one thing we could never figure out how to fix is managing our firewalls across the MPLS. The LAN interface will not respond to pings or https requests, forcing us to enable management via WAN which is awful.
For our IP based VPNs between our non-MPLS sites, we just used the setting "Allow management via this SA" on the VPN configuration, which creates access rules allowing management/ping from zone VPN to LAN, and that works perfectly.
We tried to get the same to work between the MPLS sites by creating an unused IP VPN and setting that option, but even that didn't work which leaves me with no idea what else to try.