I'm in the process of setting up a new root ADCS (Active Directory Certificate Server) certificate authority for a child domain in a multi-forest environment that already has a number of existing CAs. I would very much like to not repeat what the last guy did, which was to set stuff up in an ad hoc fashion and document nothing, so I'm looking for a way to standardize the configuration of our CAs.
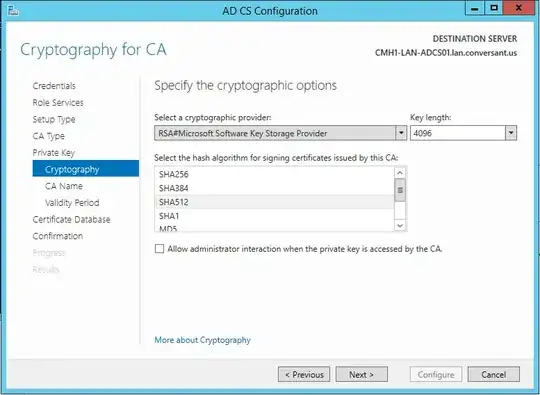
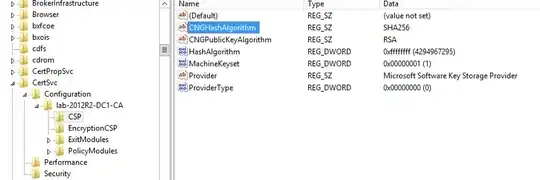
To that end, is there a way to view/export/determine the configuration of a Windows ADCS CA? In particular, the settings I can't seem to determine are the Private Key Cryptography options, as in the below setup dialogue.
The existing CAs are Server 2008 R2 or Server 2012 R2, so ideally/hopefully, I'm looking for a solution that works for both.