Before I created the new security group (id sg-abcdefg), I am able to reach the load balance from the IP address 107.178.195.144 via http. The load balancer will then forward the traffic to the backend instances. The backend instances have only one security group which allows inbound traffic from the loadbalancer group.
I want to whitelist a range of address to limit inbound traffic to the load balancer itself in AWS. Currently it is open to the world. I added inbound rules to a new security group this way
aws ec2 authorize-security-group-ingress --group-id sg-abcdefg --protocol tcp --port 80 --cidr 107.178.192.0/18
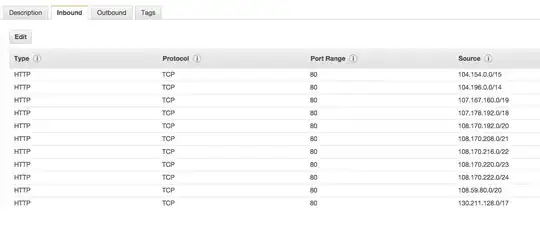
It is the final result:
However, after adding the new security group, all the traffic from 107.178.195.144 via loadbalancer to the backend instances are blocked.
I double checked and am sure that 107.178.195.144 is in the range of 107.178.192.0/18
I have added the new security group (
sg-abcdefg) to the backend instances too but it did not help.
Did I miss anything in my setup?
EDIT
It seems like the root cause is the backend instances stop receiving the health check ping. I have added 174.12.0.0/16 (the IP range of the subnet) to the sec group but to no avail