Context
Windows 2008 R2 infrastructure.
We manage network share permissions by AD security groups and put user objects in those groups.
Objective
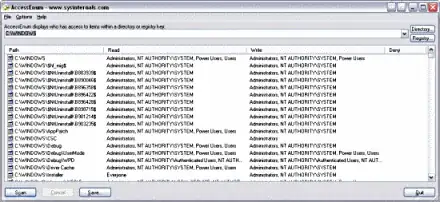
I want to see what security groups are currently assigned to each folder on a particular server. I don't want to check each folder individually by right click > Properties > Security tab.
I want to perform some function recursively so I get a result something like this:
C:\ - (DOMAIN\Group1)
C:\Folder1 - (DOMAIN\Group1)
C:\Folder1\subFolder1 - (DOMAIN\Group2)
C:\Folder2 - (DOMAIN\Group1)