In a heavily branched organization with Active Directory, I am working with the head IT department and we are delegating control to parts of the branch OU to the respective branch admins.
Our delegation concept currently handles group policies in a way that we create one group policy object under control of the head IT and one group policy object delegated to the branch admin for each of the branches, both linked on the same level to the branch OU, with the -head GPO getting the Enforced flag and the Link Order of 1.
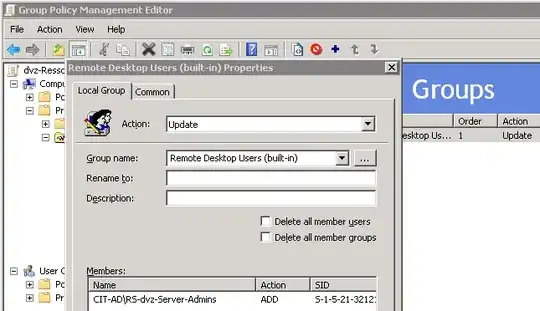
When defining local groups (usually just pre-defined groups like Administrators or Remote Desktop Users) we are facing the problem that it is rather tricky to delegate. The ultimate goal is to have whatever the -head GPO has defined in the group and merge in the -branch membership definitions. We are defining local groups via GPP in -head like this:
We are flushing the group memberships to make sure that group members which have been added once via the GPP but removed since are actually removed from the clients' local groups.
The same group might have membership definitions made via GPP in -branch:
Now the result is, that only -head's definition is ultimately present on the affected clients. We get pretty much the same result when using Restricted Groups instead of GPPs as the Enforced link flag is giving the -head GPO preference over the -branch. And when mixing Restricted Groups on -head with GPPs on -branch, we are seeing inconsistent results - depending on which CSE is running first (apparently the order of execution for CSEs is undefined), groups might or might not contain GPP-defined members from -branch.
So what would be the most sensible way to enforce certain memberships centrally while still allowing for delegation to the branch admins?