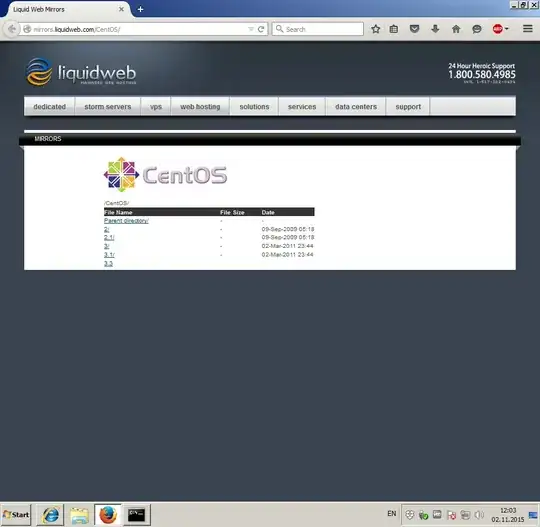
I'm trying to configure my VPS server to work as a simple HTTP proxy. I insatlled Squid 3.3.8 on CentOS 7.1.1503 and configured basic authentication with the ncsa_auth. Although the whole scheme seems to be working and i'm successfully connecting to my proxy from another PC, i'm now facing the issues with the webpage loading.
At example, when i'm trying to open http://mirrors.liquidweb.com/, webpage won't load correctly, Firefox just loads the half of it and then i see the message saying "Transferring data from liquidweb.com" for a while. Then it disappears without any result: webpage is still displayed half-loaded.
I did a little research about this problem, but the only solutions i could find were related to DNS-problems. It doesn't seem to be DNS-related problem, and adding dns_v4_first on option in my squid config hadn't made any result.
I want to especially point out that this is not a site or browser-related problem, because it showed up in all browsers i tried to open the website, and disabling the proxy in browser settings fixes the issue immediately.
It also doesn't seem to be the ISP-related problem since i can download the files through this proxy with ~50Mbps average speed. My squid.conf and the screenshot with the improperly loaded webpage are present below, thanks in advance for any guesses!
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/passwd
auth_param basic childred 5
auth_param basic realm liproxy
auth_param basic credentialsttl 2 hours
#acl localnet src 10.0.0.0/8 # RFC1918 possible internal network
#acl localnet src 172.16.0.0/12 # RFC1918 possible internal network
#acl localnet src 192.168.0.0/16 # RFC1918 possible internal network
#acl localnet src fc00::/7 # RFC 4193 local private network range
#acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl Safe_ports port 80 # http
#acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
#acl Safe_ports port 70 # gopher
#acl Safe_ports port 210 # wais
#acl Safe_ports port 1025-65535 # unregistered ports
#acl Safe_ports port 280 # http-mgmt
#acl Safe_ports port 488 # gss-http
#acl Safe_ports port 591 # filemaker
#acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
#http_access deny to_localhost
acl ncsaauth proxy_auth REQUIRED
http_access allow ncsaauth
dns_v4_first on
http_access deny all
http_port 0.0.0.0:3128
#cache_dir ufs /var/spool/squid 100 16 256
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
etc/sysconfig/iptables
*filter
# Allows all loopback (lo0) traffic and drop all traffic to 127/8 that doesn't use lo0
-A INPUT -i lo -j ACCEPT
-A INPUT ! -i lo -d 127.0.0.0/8 -j REJECT
# Accepts all established inbound connections
-A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
# Allows all outbound traffic
# You could modify this to only allow certain traffic
-A OUTPUT -j ACCEPT
-A INPUT -p tcp --dport 3128 -j ACCEPT
# Allows SSH connections
# The --dport number is the same as in /etc/ssh/sshd_config
-A INPUT -p tcp -m state --state NEW --dport 22 -j ACCEPT
# Now you should read up on iptables rules and consider whether ssh access
# for everyone is really desired. Most likely you will only allow access from certain IPs.
# Allow ping
# note that blocking other types of icmp packets is considered a bad idea by some
# remove -m icmp --icmp-type 8 from this line to allow all kinds of icmp:
# https://security.stackexchange.com/questions/22711
-A INPUT -p icmp -m icmp --icmp-type 8 -j ACCEPT
# log iptables denied calls (access via 'dmesg' command)
-A INPUT -m limit --limit 5/min -j LOG --log-prefix "iptables denied: " --log-level 7
# Reject all other inbound - default deny unless explicitly allowed policy:
-A INPUT -j REJECT
-A FORWARD -j REJECT
COMMIT