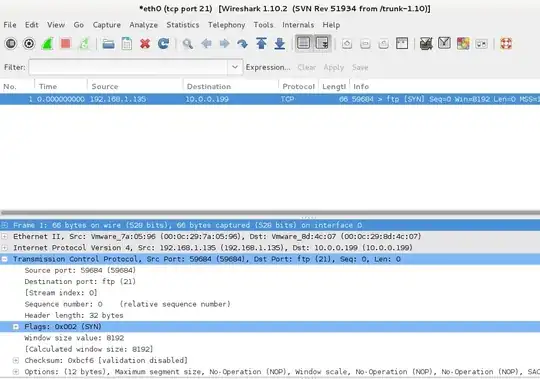
I have a pfSense box setup where my WAN interface (em0) is set up in my local network (192.168.1.100) and my LAN interface (em1) is a private network of its own (10.0.0.1). The end goal is to have the 10.0.0.x network as private malware lab where devices on that network cannot talk to anything on the 192.168.1.x network directly. Though, I would like to punch holes in the pfSense firewall to allow traffic from 192.168.1.x network to access services in the private network, such as FTP, HTTP, SMB, SSH, etc. So if I FTP to 192.168.1.100 (WAN interface) then it'll route though to the FTP server running on a device internal to 10.0.0.x. Currently I can see that my FTP server gets a TCP SYN packet, but nothing else happens.
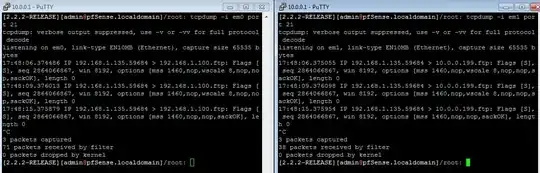
And I can see some FTP traffic through pfSense with tcpdump.
Here's my NAT port forwarding rules (they also have an associated filter rule).
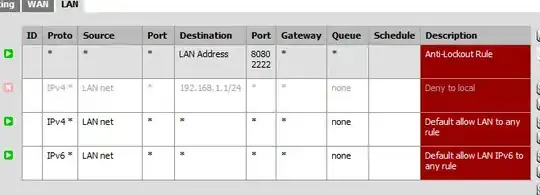
And also if it's helpful, my LAN firewall rules as well.
I thought that maybe there was an error with my blocking rules to block 192.168.1.x traffic from the 10.0.0.x network, but I have that rule disabled. I'm at a total loss and don't understand what is going wrong, so any help would be super appreciated!