What are the risks associated with import of third-party Root CA certificate into the Enterprise NTAuth Store in Windows domain except that the CA is then trusted to issue certificates?
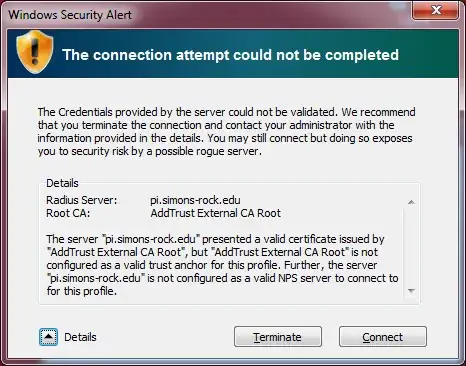
This is for test purpose to fix an issue with wireless clients getting a Windows Security Alert when connecting to a wireless network and being authenticated via new NPS server running on WS2012 R2.
The Root CA certificate is already present in computer store of the client machines under Trusted Root Certificate Authorities, but the window still appears on first connection attempt.
The goal is to get rid of the pop-up window:
EDIT: I will elaborate a little bit.
The goals:
- allow domain-joined devices to authenticate via NPS;
- use 3rd party certificate;
- users should not get Security Warning pop-up window;
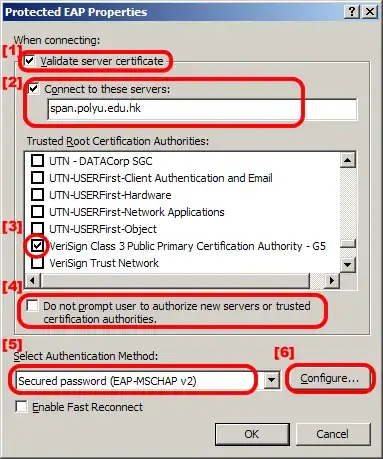
NPS on WS2012R2 is used. PEAP/MsCHAPv2 used for authentication.