I am new to Ipsec tunnels. I have successfully created a tunnel to a Cisco offsite router using a preshare key at a supplier.
In Endpoints 1 : I have the servers ip address and the remote servers ip address that I intend connecting to.
In Endpoint 2 : I have the same ip addresses as above
In the ipsec tunnel Endpoint I have listed the servers IP address and Endpoint 2 I have listed the Cisco router.
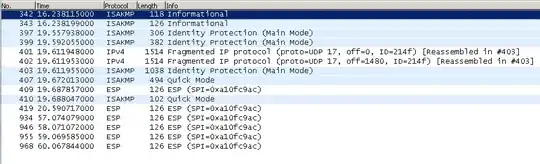
The tunnel comes up. (Its visible under monitoring and in Main Mode and Quick mode) In addition to that the supplier confirms that they can see our connection.
However when we try connect to one of the servers within their network, listed in endpoint 1 and 2 above, it does not connect.
The supplier claims that they have other clients connecting in this fashion and its not a problem on their side.
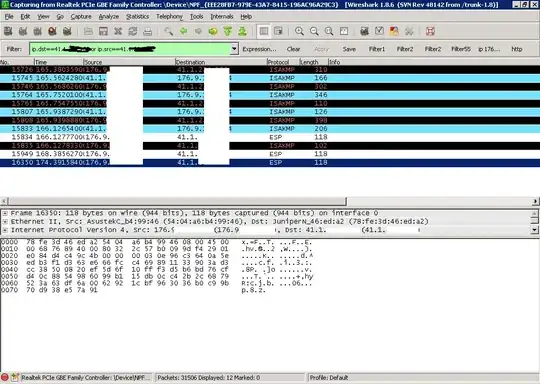
I have tried tracing the traffic in wireshark but wireshark only sees the traffic if I disable the Ipsec tunnel.
EDIT: I can see traffic to and from the tunnelendpoint when I try telnet into a server behind the tunnelendpoint. However the telnet session timesout before it is established.
Any ideas?