I installed StartSSL on my web server which is running Linux Apache on CentOS 6.5. shaaaaaaaaaaaaa.com said
Nice. example.com has a verifiable certificate chain signed with SHA-2.
However Google Chrome on Debian 7.8 said
The connection is encrypted using AES_128_CBC, with SHA1 for authentication and ECDHE_RSA as the key exchange mechanism.
On the Debian box, I did
mkdir ~/StartComCerts
mv /etc/ssl/certs/StartCom* ~/StartComCerts
and the problem went away. However, expected clients to make changes to their computers is not a workable solution. So I purchased the GeoTrust QuickSSL Premium certificate from ssls.com. Then I went to https://knowledge.geotrust.com/support/knowledge-base and it said "Certificate is installed correctly". However, when I go my site using Chrome on Debian 7.8, I get the messages:
This site uses weak security configuration (SHA-1 signatures) so your connection may not be private.
and
The site is using outdated security settings that may prevent future versions of Chrome from being able to safely access it.
I tested my site on www.ssllabs.com/ssltest/analyze.html. It rated my site with an A and said that my signature algorithm is SHA256withRSA. I went to shaaaaaaaaaaaaa.com said
Nice. example.com has a verifiable certificate chain signed with SHA-2.
I went to whynopadlock.com and everything checked out positively. I also tested with Chrome on another computer, running Windows 7, and got a green padlock with no error messages.
I don't know why I am getting the SHA-1 error on Chrome on Debian.
Edit - 2015-06-15
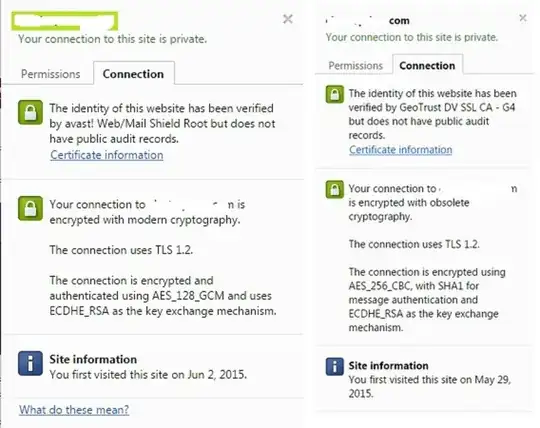
I also have an Sha-1 problem on some Windows systems. Below is the screen shot from Google Chrome on my home Windows system (left) and on my work Windows system (right). It seems to be using an Sha-1 cached certificate on different systems. I set up the intermediate certificate as per the instructions given by GeoTrust.
Edit:
I have a home business which is the purpose of my web site.