I have set up an SPF record for my domain, but I still can spoof email-addresses for my domain using fake email services like this one: http://deadfake.com/Send.aspx
The email does arrive to my gmail inbox just fine.
The email does have SPF errors in the header like this: spf=fail (google.com: domain of info@mydomain.com does not designate 23.249.225.236 as permitted sender) but it's still received just fine, which means anyone can spoof my email-address...
My SPF record is: v=spf1 mx a ptr include:_spf.google.com -all
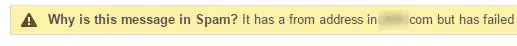
UPDATE In case anyone's interested, I have published a DMARC policy along with my SPF record and now Gmail marks spoof messages correctly (picture)