As part of implementing a SharePoint 2013 installation, I have configured SSO with ADFS on Windows Server 2012R2.
There are two separate AD forests, one as part of the Hosted SharePoint/ADFS and one onsite corporate forest.
Currently, I have the corporate AD set up as a Claims Provider Trust in the SharePoint ADFS. I am able to successfully pass through the email attribute from the corporate AD to SharePoint.
What I want to achieve is some form of claim injection from the Hosted AD Forest as part of logging on with a Corporate AD account.
Specifically, users will be members of security groups to determine SharePoint licencing. For security reasons I do not want to get this claim information from the Corporate AD as this means users will be able to change their licencing status.
So, all users will actually have an AD account in both forests. Single Sign On provided by entering their Corporate credentials as part of the sign in process.
Is there some way that I can tell my hosted ADFS to look for a user in it's own AD forest which matches the incoming Email Address Claim from the Corporate ADFS, and then inject the Role claim from the hosted forest with said email claim?
Please see the picture below for what I'm trying to achieve (Sorry for the quick MS Paint drawing!):
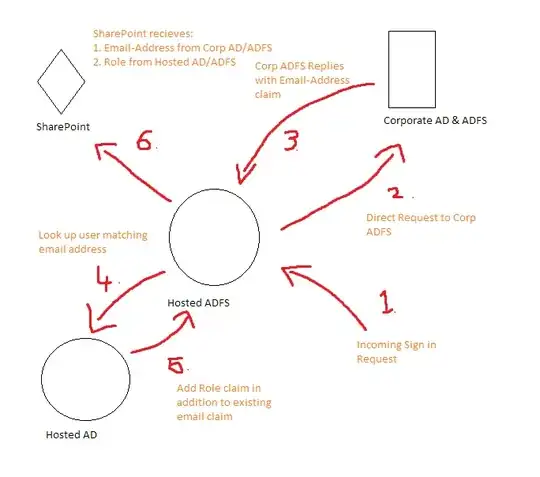
How do I achieve steps 4 & 5?
Current Claim Rules
On the Hosted ADFS, Acceptance Transform Rules for the Corporate Claim Provider Trust:
- Pass Through incoming E-mail Address claim, pass through all values
On the Hosted ADFS, Issuance Transform Rules for the SharePoint Relying Party:
- Send LDAP Attributes as Claims (UPN -> UPN, Token Groups -> Role, Email-Addresses -> Email)
- Pass Through incoming E-mail Address claim, pass through all values