Maybe the answer is yes. It is basically a hairpin NAT, attested to in Cisco page about dns doctoring.
I tried to make this work on another firewall in a different office. Below are some configuration that seems to redirect the traffic as I desired. I made these config in the ASDM, but I am only feeling my way through. I hope an expert can help me find flaws or better ideas.
I put extra comments to explain:
Result of the command: "show running-config"
...
!-- this server is monitoring the network anyway, so it is on 24/7
name 192.168.1.66 local-heartbeat.com description attempted destination for spoofed pings
!-- This is the destination that was blocked.
name 50.16.219.4 belkin.heartbeat.com description domain to redirect ping traffic
...
interface Vlan2 nameif outside security-level 0
ip address 192.168.154.100 255.255.255.0 !-- Front IP of the firewall I working on.
...
dns server-group DefaultDNS
name-server 192.168.250.254 !-- This is the dns in the greater office complex
domain-name theoraffice.local
!-- I read the next one required to allow interfaces to connect in Hairpin NAT.
!-- I don't know if this is a true hairpin, because the external belkin server
!-- is actually external.
same-security-traffic permit intra-interface
!-- Rule to allow pings to belkin
...
access-list outside_access_in extended permit icmp any host belkin.heartbeat.com
...
!-- I am behind a firewall at 1.100
icmp permit 192.168.1.100 255.255.255.252 outside
...
nat-control
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
...
!-- This rule is the one that redirects the ping, when I ping with domain name.
static (outside,inside) local-heartbeat.com belkin.heartbeat.com netmask 255.255.255.255 dns
...
That is working when I ping to belkin.com. Example:
[auser@192.168.2.20]$ ping heartbeat.belkin.com
Pinging heartbeat.belkin.com [192.168.1.66] with 32 bytes of data:
Reply from 192.168.1.66: bytes=32 time=2ms TTL=63
Reply from 192.168.1.66: bytes=32 time=19ms TTL=63
Reply from 192.168.1.66: bytes=32 time=20ms TTL=63
Reply from 192.168.1.66: bytes=32 time=11ms TTL=63
Ping statistics for 192.168.1.66:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 2ms, Maximum = 20ms, Average = 13ms
In that test, the ping came back from the local server.
Here are config screenshots.
Setting to allow hairpin NAT.
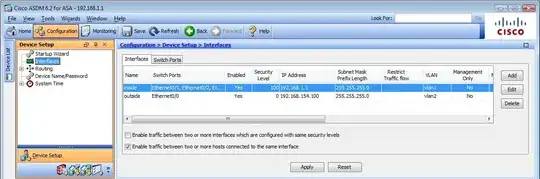
Allows a ping attempt to the outside heartbeat server.
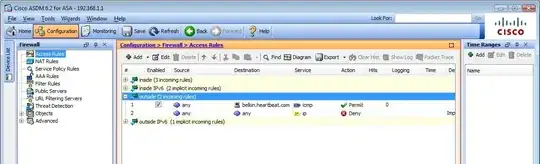
Hairpin NAT Rule redirecting the attempt to the local host.

To test it, I removed the only the hairpin NAT rule, then did ipconfig /flushdns on the windows laptop and tried to ping belkin.com.
[auser@192.168.2.20]$ ping heartbeat.belkin.com
Pinging heartbeat.belkin.com [50.16.219.4] with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 50.16.219.4:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
Now I have two other questions.
First, with the hairpin removed, the ping headed for belkin, and was blocked. This is good, but it surprises me. Why is it blocked, though I made the rule to allow earlier and did not change that access rule at this point?
Second, why did this question get a downgrade?


