I am sending 4 bytes of data over UDP upon request from another program. Sometimes the frame's protocol is identified as STUN in Wireshark, but I have no clue why.
A ruby prototype of the communication looks like this(simpled down as much as possible for clarity)
The requesting code:
require 'Socket'
sock = UDPSocket.new
loop do
sock.send "req", 0, "127.0.0.1", 40004
x = sock.recvfrom 4
dataLength = x[0].unpack('L')[0]
received = 0
sleep 2
end
The answering code:
require 'Socket'
sock = UDPSocket.new
sock.bind "127.0.0.1", 40004
loop do
x = sock.recvfrom 3
if x[0] == 'req'
sock.send [(Random.rand 10000..300000)].pack('L'), 0, "127.0.0.1", x[1][1]
end
end
When analizing this communication in Wireshark, it shows that the frames sent by
sock.send [(Random.rand 10000..300000)].pack('L'), 0, "127.0.0.1", x[1][2]
are sometimes identified as plain UDP, sometimes as STUN. I noticed that 2 most significant bytes of the STUN frames I checked have values of 0x00, bet some plain UDP frames also have 2 most significant bytes with value of 0x00.
Image of a STUN frame:
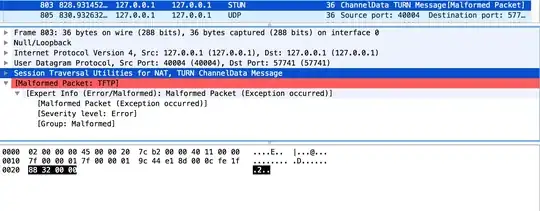
Image of a plain UDP frame: 
Why is this happening?