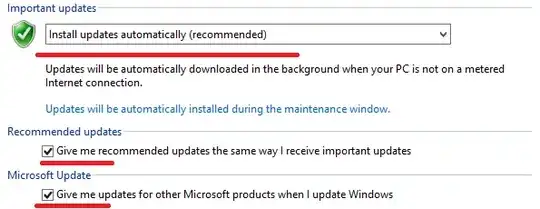
You may do better to build a Powershell DSC to enforce this policy, and apply that to the newly built server instances. Based on my readings of http://technet.microsoft.com/en-us/library/dd939844(v=ws.10).aspx, it looks like you could solve this with:
WindowsAutoUpdate Policy {
Node localhost {
Registry EnableSilentUpdates
{
Ensure = "Present"
Key = "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU"
ValueName = "AUOptions"
ValueData = "4"
ValueType = "Dword"
}
Registry ScheduledInstallDay
{
Ensure = "Present"
Key = "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU"
ValueName = "ScheduledInstallDay"
ValueData = "0"
ValueType = "Dword"
}
Registry ScheduledInstallTime
{
Ensure = "Present"
Key = "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU"
ValueName = "ScheduledInstallTime"
ValueData = "00:00:00" ## Midnight. Pick another
ValueType = "Dword"
}
Registry AlsoGetNonCriticalUpdates
{
Ensure = "Present"
Key = "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU"
ValueName = "IncludeRecommendedUpdates"
ValueData = "1"
ValueType = "Dword"
}
Registry EvenTheReallyMinorUpdates
{
Ensure = "Present"
Key = "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU"
ValueName = "AutoInstallMinorUpdates"
ValueData = "1"
ValueType = "Dword"
}
}
}
I could find the registry entries to update other Microsoft packages, but the methodology I used to get those last two registry entries was to take a registry snapshot beforehand
regedt32 /e "pre.txt" "HKEY_LOCAL_MACHINE\Software\"
, changed those settings and took another registry snapshot
regedt32 /e "post.txt" "HKEY_LOCAL_MACHINE\Software\"
and compared the two using regdiff (
https://code.google.com/p/regdiff/).