First off, I'm sorry if this is vague, but I'm not very familiar with DNS or DNS terminology.
What I'm trying to do:
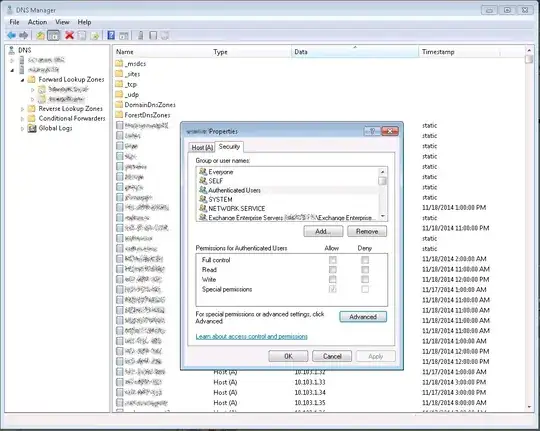
I want to limit what hostnames are allowed to dynamically update DNS. I don't want to end up with a malicious user sending a dynamic DNS update with the same hostname as a domain controller or radius server or something.
Here's why this is a problem:
We run a mixed environment shop and have a lot of devices that aren't tied to AD, so I can't limit DNS updates to secure-only.
Can someone please tell me how to fix this and what it's called? DNS is running on Windows Server 2008 R2 domain controllers.