I'm learning about a bit more about firewalld and I've been able to create an unsafe network to where I can connect from my internal network, but now, I'm stuck trying to prevent the unsafe network from reaching my internal network.
Here's an image of the topology of the network (most of the internal network is virtualised and all of the unsafe network is virtualised):
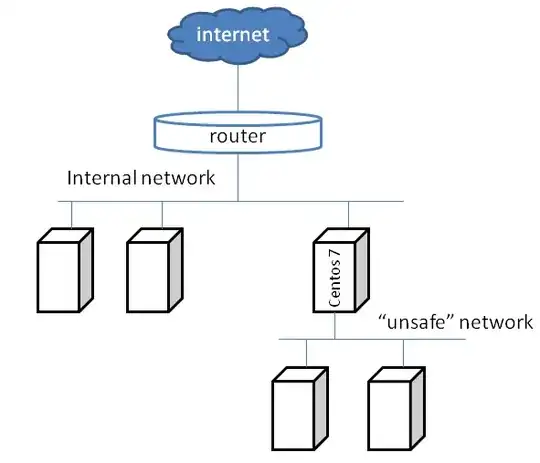 .
.
On the Centos7 box that connects the 2 networks, I configured IP forwarding and added a direct rule (same as in this question). The nodes on the unsafe network have Centos7 as the default gateway (with the idea that those boxes will be allowed to access the internet, but not the internal network).
With the above, the nodes in the internal network can access the unsafe network, but the unsafe network can still access some IPs on the internal network (in particular the Centos7 IP address on the internal network and also the IP of the vmware host in the internal network). Apart from those 2, the "unsafe" network cannot reach any of the other IPs in the internal network.
So finally, the question is, can I reject anything coming from the unsafe network that has as a destination the internal network?