I took over an exchange 2010 server on what I believe is a Hyper V Virtual Machine, running Windows Server 2008. We have a SonicWALL firewall, but the majority of the licensing on the firewall is no longer paid for (I think it's minimal spam protection if anything). We are having a major problem with spam, we have apx. 100 email addresses. I'm just looking for a way to stop all my spam, not sure if Exchange has built-in functionality that can be utilized easily.
Asked
Active
Viewed 133 times
-1
-
Are you using the built-in anti-spam components of Exchange? – joeqwerty Oct 03 '14 at 17:12
-
2I know what you are looking for, but you haven't really asked a question here. If you are looking for product recommendations, those are generally off topic here. – Rex Oct 03 '14 at 17:29
-
Yes, I am using the built-in anti-spam components of Exchange. – TheFrack Oct 06 '14 at 15:52
1 Answers
4
Are you using DNSBLs? Like Spamhaus or Barracuda's? If not, start there, that'll cut spam down by 90% or more.
To enable DNSBLs:
- On the server, open EMS and run
C:\Program Files\Microsoft\Exchange Server\V14\Scripts\install-AntispamAgents.ps1 - Run
sc stop MSExchangeTransportandsc start MSExchangeTransport - Close and reopen EMC or EMS if any are open.
In EMC: Organization Configuration -> Hub Transport, Anti-Spam tab, IP Block List Providers, Properties...
Add providers as desired...
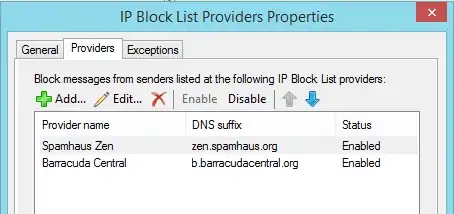
Make sure you edit the error message under each and provide a good explanation of why a sender would be blocked, like "Your IP is listed in Spamhaus. See http://www.spamhaus.org/lookup/ for details."
Chris S
- 77,945
- 11
- 124
- 216
-
I had a ton of DNSBLs already. I had a lot of outdated ones though, so I made it so I have Spamhaus Zen, Barracuda Central & SpamCop. But, even after doing that, I just received another one. Could one of the computers on my network have a virus? If so, how would I track it down? Here are some of the IP's that I see in the headers: 23.229.62.180 138.128.13.131 138.128.13.135 138.128.13.139 94.155.113.6 94.155.113.9 – TheFrack Oct 06 '14 at 15:22
-
DNSBLs are a great first step, but still let a fair amount of spam through. Those IPs really don't stand out in any way, other than being typical hosting sites that get abused to send spam. You'll want to add some kind of heuristic spam protection, the easiest way is to use a filtering service provider. An alternative is to install something locally - MS's "recommended" solution is Forefront Protection for Exchange (either hosted or on-premise). – Chris S Oct 06 '14 at 17:13
-
Thanks. Our email is pretty sensitive as it contains legal documents and high sensitivity/private information on a regular basis. Do you know if Microsoft Forefront or other solutions that integrate with exchange are better than stand alone implementations typically? – TheFrack Oct 07 '14 at 18:06
-
Solutions that integrate with Exchange usually also integrate with the Outlook client so that users can flag spam or block senders within Outlook and have that enforced by the server. Other than that I they aren't any better at catching spam in my experience. For the last month Cloudmark has been the target of spammers, so more spam is getting through Forefront for Exchange than usual (FfE is powered by Cloudmark); but next month it will be someone else and so the game goes. – Chris S Oct 07 '14 at 20:11