I've set up a TOR proxy but I can't access to the .onion sites. I do surf through the TOR net though.
I set up a PPTP VPN (I know it's insecure but it's just a test) to create a quick IP address swap so I get a 192.168.1.{50 - 60} IP which I will route through the TOR net.
Server: Debian 7.6
Client: Windows 7
This is my torrc conf:
DNSPort 192.168.1.250:5300
TransPort 192.168.1.250:8118
VirtualAddrNetworkIPv4 10.192.0.0/11
AutomapHostsOnResolve 1
AutomapHostsSuffixes .exit,.onion
This is my iptables conf:
DNAT udp -- anywhere anywhere source IP range 192.168.1.50-192.168.1.60 udp dpt:domain to:192.168.1.250:5300
DNAT tcp -- anywhere anywhere source IP range 192.168.1.50-192.168.1.60 tcp dpts:tcpmux:65535 to:192.168.1.250:8118
netstat -untap output:
tcp 0 0 192.168.1.250:8118 0.0.0.0:* LISTEN 16027/tor
tcp 0 0 127.0.0.1:9050 0.0.0.0:* LISTEN 16027/tor
tcp 0 0 192.168.1.250:59864 X.X.X.X:443 ESTABLISHED 16027/tor
tcp 0 0 192.168.1.250:48069 X.X.X.X:9001 ESTABLISHED 16027/tor
tcp 0 0 192.168.1.250:39310 X.X.X.X:8443 ESTABLISHED 16027/tor
udp 0 0 192.168.1.250:5300 0.0.0.0:* 16027/tor
PPTP router conf:
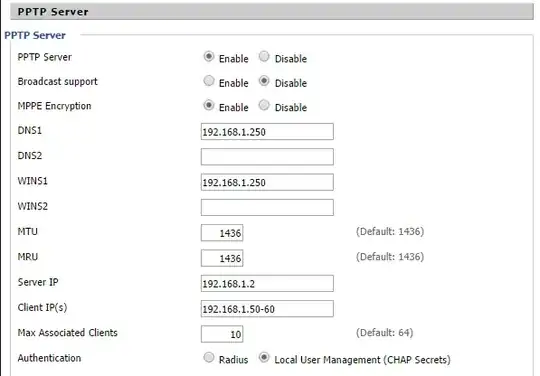
This is what happens when I try to query a .onion website:
listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
11:59:40.870407 IP 192.168.1.50.57575 > 8.8.8.8.53: 36750+ A? google.com. (28)
11:59:41.105780 IP 8.8.8.8.53 > 192.168.1.50.57575: 36750 1/0/0 A 74.125.232.233
****UPDATE**:** If I DO NOT use the PPTP VPN everything work as expected.
I do not understand why 192.168.1.50 still queries 8.8.8.8:53 when there's the according iptables rules which prohibits it and, furthermore, redirects the packet it to the TOR port.
UPDATE 2, firewall:
Chain INPUT (policy ACCEPT 524K packets, 123M bytes)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- * * 0.0.0.0/0 10.2.3.1 multiport dports 58050,58051,9091,80,22,139,445,5900,5901,5222,8200
Chain FORWARD (policy ACCEPT 56226 packets, 8404K bytes)
pkts bytes target prot opt in out source destination
0 0 DROP all -- * * 10.2.3.0/24 10.2.2.0/24
0 0 DROP all -- * * 10.2.3.0/24 10.2.1.0/24
Chain OUTPUT (policy ACCEPT 631K packets, 511M bytes)
pkts bytes target prot opt in out source destination
Chain LOG_AND_DROP (0 references)
pkts bytes target prot opt in out source destination
Thank you very much!