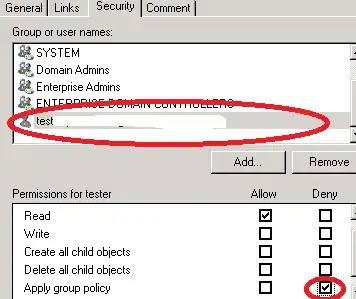
I have an issue which i need some help with.
Current Scenario:
I have a domain firewall policy, which turns the firewall ON and is enforced on "Authenticated users". The domain policy locks the firewall with the "For your security, some settings are managed by your system administrator." for all users. This is not to be changed.
Screenshot: https://www.dropbox.com/s/aa01il1zjjgoa05/GPO_firewall.png?dl=0
Change wanted:
However, now i have a SPECIAL user, which needs to be able to administrate the client firewall all by himself, so the settings must NOT be "For your security, some settings are managed by your system administrator" locked... They must be open for edit by this user on his laptop ONLY!
My queation is:
What would the best and easiest way to set this up?
Thx