We are trying to replicate what is described at https://doc.pfsense.org/index.php/Routing_internet_traffic_through_a_site-to-site_IPsec_tunnel#Set_up_the_IPsec_tunnel_Phase_2
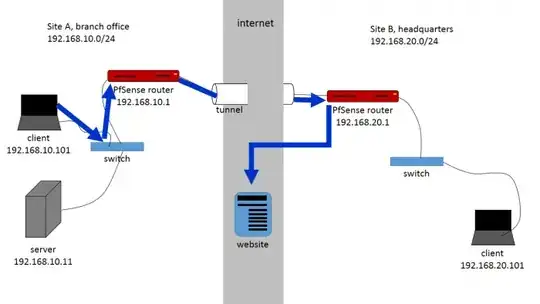
We are using 2 Fortinet Fortigate firewalls. We previously had a functioning ipsec vpn between the two sites but LAN to LAN only. ie. Site A LAN to Site B LAN and vice versa. We have tried modifying the IPsec tunnels to also carry WAN bound traffic, but it seems to still go across Site A WAN directly.
Our configuration:
12.34.56.0/24 is Site B IP block
Site A (Branch office):
Phase 2: Local: 172.20.10.0/24 Remote: 0.0.0.0/0.0.0.0
Policy:
- internal --> siteB, source ALL, destination, ALL
- SiteB --> internal, source ALL, destination, ALL
Site B (Datacenter)
Phase 2: Local: 0.0.0.0/0.0.0.0 Remote: 172.20.10.0/24
Policy:
- internal --> siteA, source ALL, destination, ALL
- SiteA --> WAN, source ALL, destination, ALL, NAT dynamic IP pool 12.34.56.1
In addition to outbound traffic as the image depicts we would also like inbound traffic from the same IP or multiple to be directed back to Site A. So for example if site A is hosted a web page and someone goes to 12.34.56.1 it will be directed to site A server.