I am another such lazy and inexperienced person. I can't use wireguard or vxlan tunnels because I don't know up front all my VPN clients (to predeclare point-to-point tunnels) and my clients don't share an l2 segment with the VPN server (that would allow for multicast vxlan). Moreover, I can't easily tunnel through NAT with vxlan. Finally, I might want to connect from a macOS computer. So, OpenVPN it is.
Server config
Create the certificates. Public certificate for the server is sufficient. You can either use easy-rsa, or you can do it on your own with openssl. I prefer openssl.
On RHEL 9, do this
dnf install -y https://dl.fedoraproject.org/pub/epel/epel-release-latest-9.noarch.rpm
dnf install -y openvpn easy-rsa openssl
When using easy-rsa, that got installed into
/usr/share/easy-rsa/3.0.8/easyrsa
When using openssl, create certificate authority and server certificate.
Use the -nodes parameter for openssl to avoid having to specify password for the generated certificates.
openssl req -nodes -x509 -newkey rsa:4096 -sha256 -days 3650 -keyout ca-key.pem -out ca-cert.pem -subj "/CN=TestCA"
openssl req -nodes -newkey rsa:4096 -keyout server-key.pem -out server-csr.pem -subj "/CN=localhost"
openssl x509 -req -in server-csr.pem -CA ca-cert.pem -CAkey ca-key.pem -out server-cert.pem -days 365
openssl dhparam -out dh.pem 2048
Create config following the sample in https://github.com/OpenVPN/openvpn/blob/master/sample/sample-config-files/server.conf
proto udp
dev tun
ca ca-cert.pem
cert /root/server-cert.pem
key /root/server-key.pem
dh /root/dh.pem
verify-client-cert none
auth-user-pass-verify /bin/true via-env
script-security 3
server 11.8.0.0 255.255.255.0
push "route 11.0.0.0 255.0.0.0"
push "redirect-gateway local"
topology subnet
explicit-exit-notify 1
Now run server with
# openvpn --config openvpn.config
2023-07-20 23:32:55 WARNING: Compression for sending and receiving enabled. Compression has been used in the past to break encryption. Allowing compression allows attacks that break encryption. Using "--allow-compression yes" is strongly discouraged for common usage. See --compress in the manual page for more information
2023-07-20 23:32:55 --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
2023-07-20 23:32:55 WARNING: POTENTIALLY DANGEROUS OPTION --verify-client-cert none|optional may accept clients which do not present a certificate
2023-07-20 23:32:55 OpenVPN 2.5.9 x86_64-redhat-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Feb 16 2023
2023-07-20 23:32:55 library versions: OpenSSL 3.0.7 1 Nov 2022, LZO 2.10
2023-07-20 23:32:55 WARNING: --keepalive option is missing from server config
2023-07-20 23:32:55 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
2023-07-20 23:32:55 TUN/TAP device tun0 opened
2023-07-20 23:32:55 net_iface_mtu_set: mtu 1500 for tun0
2023-07-20 23:32:55 net_iface_up: set tun0 up
2023-07-20 23:32:55 net_addr_v4_add: 11.8.0.1/24 dev tun0
2023-07-20 23:32:55 Could not determine IPv4/IPv6 protocol. Using AF_INET
2023-07-20 23:32:55 UDPv4 link local (bound): [AF_INET][undef]:1194
2023-07-20 23:32:55 UDPv4 link remote: [AF_UNSPEC]
2023-07-20 23:32:55 Initialization Sequence Completed
Client config
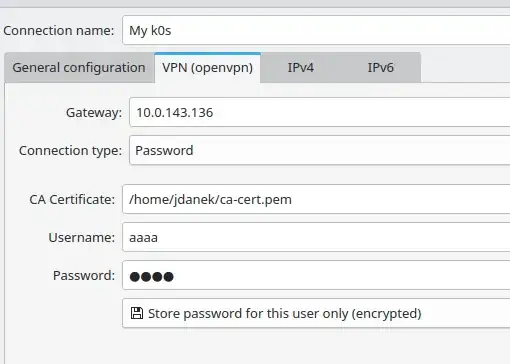
Copy ca-cert.pem to all clients. Then configure clients in the NetworkManager GUI for KDE.
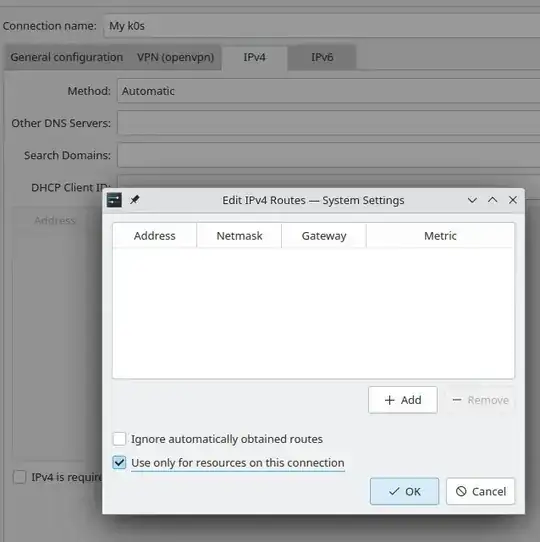
Don't forget to enable "Use only for resources on this connection", from https://serverfault.com/a/469131/116739, otherwise all your traffic will go through the VPN by default, which you may not want.