I'm incredulous as to whether KVNO has anything to do with your problem, OK maybe with Linux clients, but anyway, use Wireshark/Network Monitor:
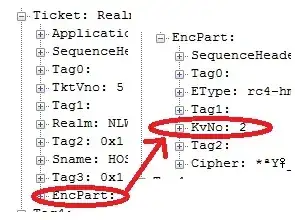
Key Version Numbers are described in MS-KILE section 3.1.5.8.
By the way, Mathias R. Jessen is correct in that in that Windows typically ignores KVNOs. But they are still implemented in an RFC-complaint way.
https://docs.microsoft.com/en-us/archive/blogs/openspecification/to-kvno-or-not-to-kvno-what-is-the-version
No, Windows does not pay attention to KVNO. It simply ignores it.
But the KVNO does have some significance in an RODC environment:
https://docs.microsoft.com/en-us/archive/blogs/openspecification/notes-on-kerberos-kvno-in-windows-rodc-environment
Some more info here: https://web.archive.org/web/20150204183217/http://support.microsoft.com/kb/2716037
In an environment with one or more RODCs authentication may fail when
interacting with certain MIT based Kerberos devices in one of the
following scenarios.
· The client is an MIT device which received a TGT from
Windows KDC on RODC
· The client passes a TGT generated by Windows KDC on RODC to
MIT Device which in turn uses the TGT to request a TGS on behalf of
the calling user.
In both scenarios the TGT will have been issued by an RODC where the
msDS-SecondaryKrbTgtNumber associated with the krbtgt account for that
RODC will have a value greater than 32767.
