When using 802.1x certificate-based authentication on Windows machines, should I use different certificate for each machine?
Yes, otherwise you may as well be using a shared passkey. Having a different certificate for each machine (or user) is how you prevent clients from being able to decrypt each others' traffic.
If I should, how do I distribute these certificates for hundreds of computers? Does this always require manual intervention?
Actually, the typical method is a GPO that assigns the machine a certificate signed by the internal certificate authority.
What you're looking for are the Computer Configuration -> Windows Settings -> Security Settings -> Public Key Policies section under Group Policy Management.
There is a fair bit of setup involved on your part, but once you get it running, it is relatively maintenance-free, and very automagical. I've attached a screenshot below of our certificate-related Group Policy settings to give you an idea of what's involved.
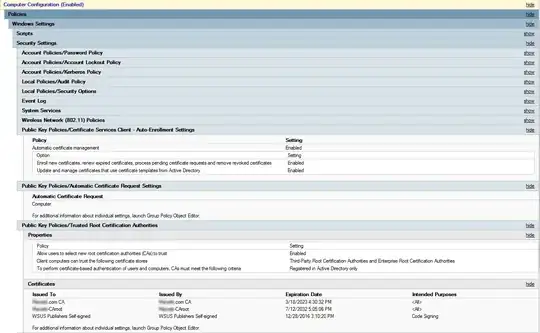
Notice the unexpanded Wireless Network (802.11) Policies Group Policy settings; this is where I define the wireless network and set our wireless clients to auto-join it. I have a couple ADDS Certificate Authorities set up, and then made trusted by all machines in the Public Key Policies/Trusted Root Certification Authorities. The certificate request is generated automatically, and clients are enrolled automatically, according the machine certificate template I've created (on our Certificate Authorities).
This setup does mean that computers have to connect to the domain and get their certificate before they can use the RADIUS-authenticated wireless network, but that's handled when the machine is initially imaged, and why there typically isn't a problem pushing certs out via Group Policy - to join the domain, you have to be able to connect to it, so a certificate can be created and assigned at that time.
Just as quick word of warning, be careful with those auto-enrollment settings (and test first), or you might end up like my dumb ass did, with hundreds of thousands of certificates you can't revoke, because you're issuing a new one on every logon and startup. (Oops!)
