I have a remote server that I can only access through RDP. It uses a proper SSL certificate from godaddy for RDP, not a self signed one. The server is 2008R2, and I believe is set to the default of requiring network level authentication. Unfortunately, I do not have any lights out management features or IPKVM on this server.
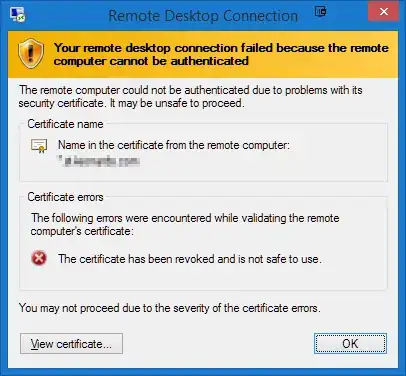
Due to heartbleed, I revoked all my certificates and reissued them. Unfortunately, I clearly missed setting RDP up for this new certificate. Now I get "This certificate has been revoked and is not safe to use", and "You may not proceed due to the severity of the certificate errors".
I know the certificate is revoked. That's why I'm trying to get in to fix it! But I can't replace the certificate until I can remote in. And I can't remote in until I replace the certificate.
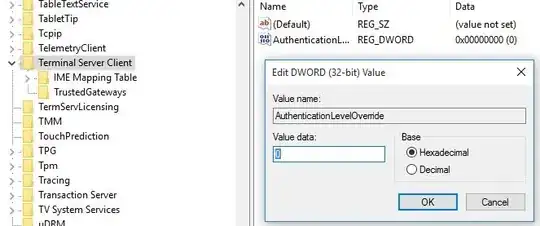
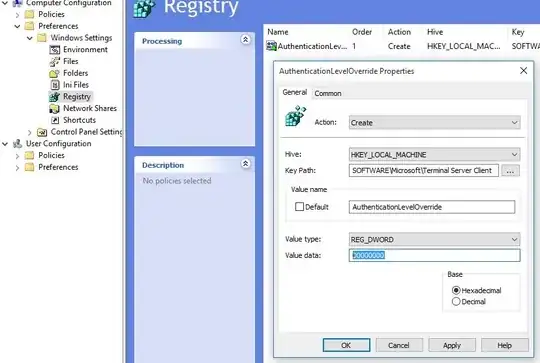
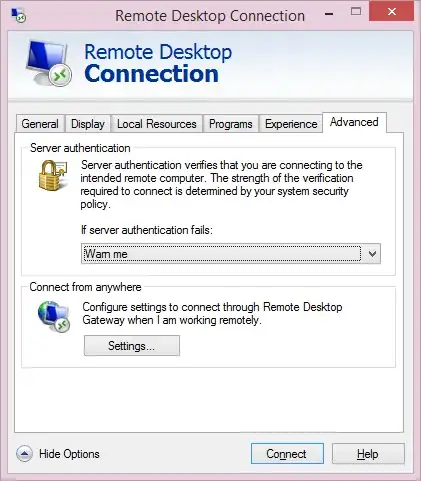
Is my only option to drive there and login from the console, or is there a way to temporarily ignore the certificate error?