#Get user names that have logged onto workstation
$Users = gwmi win32_networkloginprofile | where {$_.name -match "EXP\\"} | where {$_.name -notmatch "srvtasksched"}
$Users | foreach{
$Name = $_.Name
$LastLogon = $_.LastLogon
$LogonTime = [System.datetime]::ParseExact($LastLogon.Substring(0, $LastLogon.IndexOf(".")), "yyyyMMddHHmmss", [System.Globalization.DateTimeFormatInfo]::InvariantInfo)
if($(Get-Date).Subtract($LogonTime).TotalDays -ge 14)
{
#User hasn't logged into workstation in over 2 weeks
#Get profile path
$UserSID = $(New-Object System.Security.Principal.NTAccount($Name)).Translate([System.Security.Principal.SecurityIdentifier]).Value
$UserRegKey = GCI 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList' | where {$_.Name -match $UserSID}
$ProfilePath = $(Get-ItemProperty $UserRegKey.PSPath -Name ProfileImagePath).ProfileImagePath
Write-Host "Deleting User $Name"
gwmi win32_userprofile | where {$_.SID -eq $UserSID} | foreach {$_.Delete()}
}
}
That's the script. It detects and deletes domain profiles (Domain is EXP) on systems that haven't logged into the system in over 14 days, and it works.
However, I started receiving complaints that the script is deleting local accounts, one local account in particular. Assuming that was impossible (I have perfect script skills, right?), I took a look, ran the script, and saw that the profile folders for all the local accounts were still present under C:\Users (Win 7 workstations). False claim.
Fast forward, more complaints. I ran the script again, same results. However, this time I noticed that the registry entry for one particular local account was gone (the one the complaints are stemming from). I ran the script pretty much line by line after that, breaking down the $Users | foreach{ loop, making sure it grabs the correct sids and runs Win32_UserProfile.delete() on the right SIDs, it does.
However, when running the script (it's a sched task so I ran it 'manually' from there), that same local SIDs is deleted, and all the rest remain, which adds to the confusion; because when watching the action, I see the domain user folders under C:\Users delete immediately, but the local ones remain, adding to the confusion.
At first I thought this was limited to a single local profile, however after opening the registry I noticed HKEY_USERS only had a couple entries:
My domain account from connecting remotely, and
The problem account I logged into to verify the account still existed, even though the profile didn't.
All the other SIDs, local or domain, were gone. It is limited to a single local user account.
The effects of this of course is that when someone logs into a local account, everything in their profile folder is overwritten, however watching the script run and delete all profile folders of domain accounts but not local accounts is a bit misleading.
Update
I removed and updated info above. Also, pictures are worth a thousand words, so here goes:
- Shot of Profile List Reg Key and C:\Users before running script. The partially blank SIDs are tied to domain accounts, and the highlighted profile folders are to domain users:
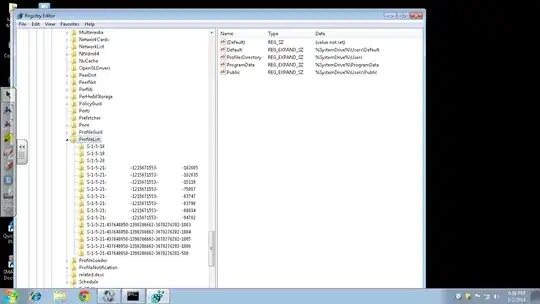
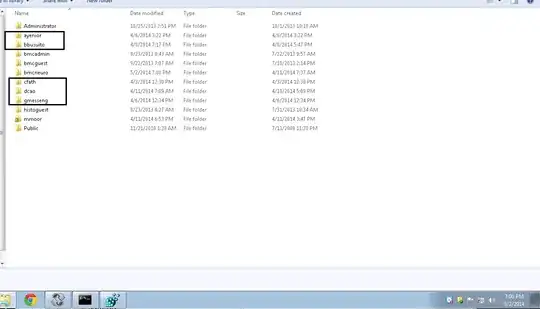
- Shot of same, after script runs. One domain SID left, which is mine:
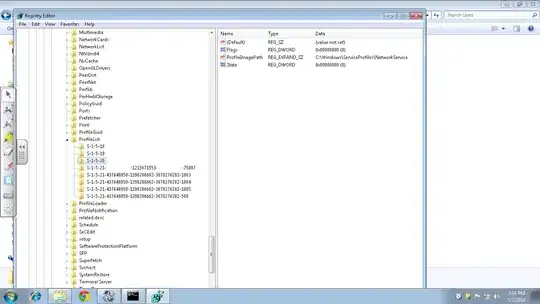
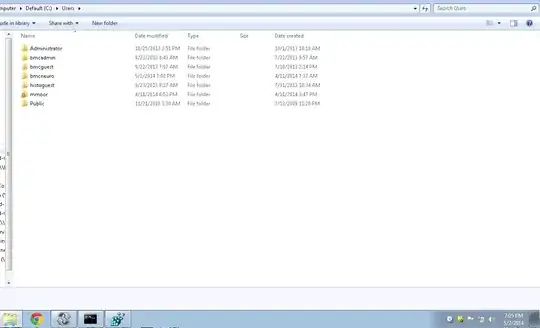
For clarification, I want to know why a local account is being deleted when this script runs. It seems like either
No local accounts would be deleted (script runs as intended)
All local profiles would be deleted (script doesn't discriminate against one local account, even if that means it also doesn't run as intended).