How can I access port 10000 on Amazon Web Services? I added port 10,000 to a security group, but I still cannot access it.
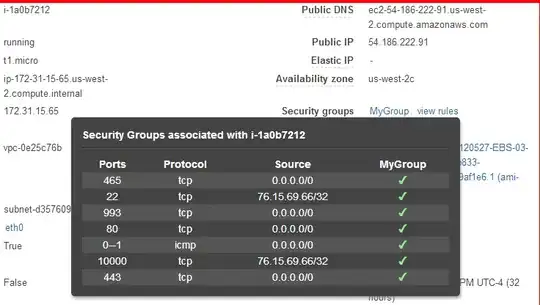
I can only access the service locally.
[root@ip-172-31-15-65 ~]# curl -I http://localhost:10000
HTTP/1.0 200 Document follows
Date: Sat, 5 Apr 2014 03:03:40 GMT
Server: MiniServ/1.680
When I try from my external (to AWS) IP, then it doesn't work.
$ curl -I http://54.186.222.91:10000
curl: (28) Connection timed out after 300138 milliseconds
Here is netstat
[root@ip-172-31-15-65 ~]# sudo netstat -tunlp |grep 10000
tcp 0 0 0.0.0.0:10000 0.0.0.0:* LISTEN 14258/perl
udp 0 0 0.0.0.0:10000 0.0.0.0:* 14258/perl
Here is iptables. It's a brand new instance.
[root@ip-172-31-15-65 ~]# sudo iptables --list
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
For some reason, this command fixed it. I don't understand why because line 1 and 3 already accepts all.
iptables --delete INPUT 5
Here is verbose iptables
[root@ip-172-31-15-65 postfix]# iptables -L -nv
Chain INPUT (policy ACCEPT 3348 packets, 173K bytes)
pkts bytes target prot opt in out source destination
89357 80M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
102 5883 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
14 2248 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 50224 packets, 17M bytes)
pkts bytes target prot opt in out source destination