I set up a VPN tunnel to my web server targetting its FQDN: (e.g. my.server.com) using the built-in Windows 7 VPN feature and the built-in Windows 8 Routing and Remote Access (RRAS) VPN feature.
How do I ensure that all traffic targetting the FQDN "my.server.com" is routed through the VPN tunnel? Specifically, if I typed \\my.server.com\sharedfolder into the Explorer address bar or map a shared drive in explorer to such a path, I want the traffic to go through the VPN associated with my.server.com.
Basically, I want Windows to be smart enough to route traffic to "my.server.com" over the encrypted VPN when the VPN to "my.server.com" is connected, and to route it normally when it's not connected. Is that too much to ask?
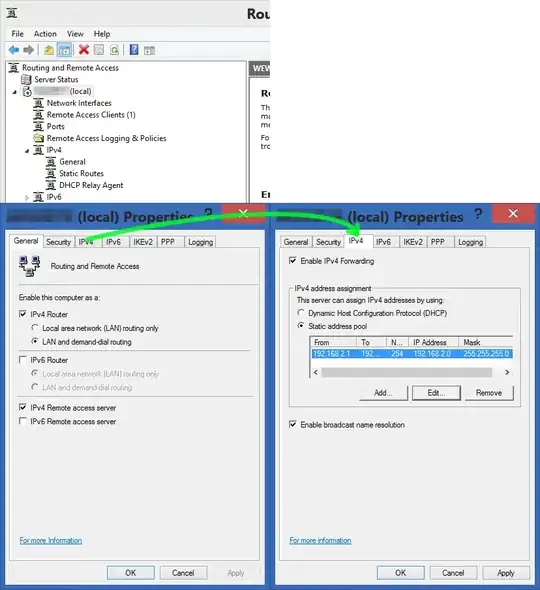
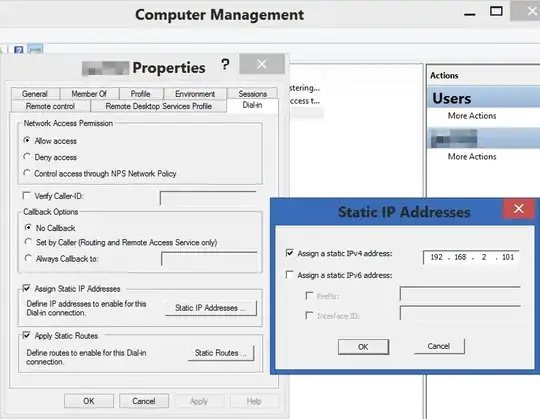
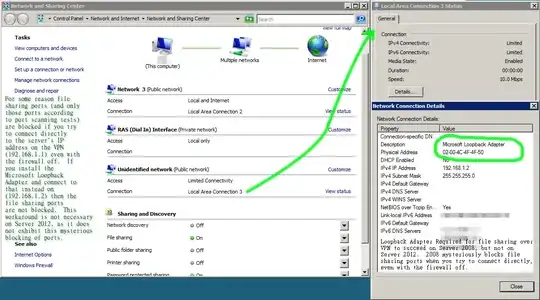
It seems to me that once connected, the VPN gets a local IP address like 192.168.1.101 (which I've assigned statically on the server in the dial-in tab of my user account properties), and targetting that address does route the traffic over the VPN. It seems that traffic targetting "my.server.com" is never routed over the VPN and is treated separately from the VPN's IP address, and I have to use that VPN IP address to route things over the VPN. The only benefit to that is the firewall can be configured so that file-sharing traffic can originate only from that IP address.
There are two problems with that setup:
- Traffic targetting "my.server.com" is not automatically routed over the VPN, which is insecure and confusing because the VPN is active. It's non-intuitive.
- Windows explorer tends to let drive connections time out when using
a local subnet address like
\\192.168.1.101\sharedfolderand Explorer freezes for a good 30 seconds when I try to access the drive again. It's really annoying, and the problem does NOT occur when the drive is mapped using the FQDN like\\my.server.com\sharedfolder... but then it's not routed over the VPN!
How can I solve this problem?
Update: I also notice the following when I have 2 VPN's connected, one with static IP 192.168.1.101 and the other with 192.168.1.102. With both VPNs established and both set to NOT use the default gateway on the VPN, and both VPNs showing those two independent IP addresses in their connection status, Explorer gets confused, cannot connect to the 2nd one, and then if I open a new window and try to go to the 2nd address, it seems to equate it with the first one and from then on both addresses (101 and 102) access the same folder on one server over the first VPN. It makes no sense.