Ok, so first off... I have done this multiple times with VMware and had zero problems so I assume I am missing something in Hyper-V.
Hardware I am working with:
- Single Dell R510 Host
- Onboard Dual Port Nic
- Quad Port Intel Nic
- 2x D-Link DES-1228 Switch
Immediate Goals:
- Dedicated Management (done)
- 1 Intel Port for LAN0 and 1 W7 Guest on network (done)
- 1 Intel Port for LAN1 and 1 W7 Guest on network (problem)
* NOTES *
- LAN0/Management same subnet
- LAN0 has DHCP server / LAN1 Strictly Static
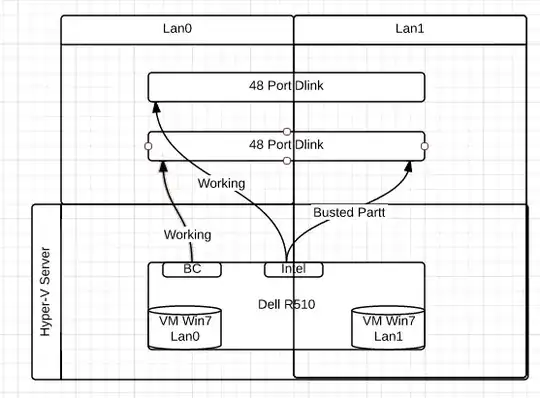
- LAN0 and LAN1 are VLAN'd on D-Link as LAN0 - 01 - default, LAN1 - 02 - lan1
- Interface 0(LAN0) is on D-Link #1 and Interface 1(LAN1) is on D-Link #2
Now my issue...
When setting up the 3rd interface for LAN1 I have somehow un-intentionally created a broadcast storm or something and stopped almost all LAN1 traffic. There is a small chance that it could have been spanning tree doing something weird (so says my CIO after disabling the interface and Guest) but I would not think that would cause such a huge problem.
Settings are fairly straight forward, but since I cannot leave the network in that condition I cannot troubleshoot. I do not like that I cannot modify Physical NIC settings within the HV Host. I noticed after I was forced to disable the Guest and Adapter using LAN1 that there was VLAN Identification for management operating system. Does this need to be enabled to isolate the VLAN traffic??
Please excuse my ignorance of Hyper-V if I missed something simple
As for the configuration, I removed what I had configured during the storm or possibly spanning tree craziness, so what I have now is different. What was configured yesterday that I "thought" was going to work looked a bit like this, but the 2 additional Virtual Networks (all configured the same, but wired a bit differently.
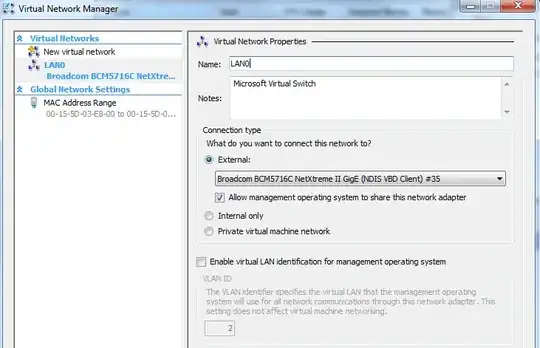
3x Virtual Networks - All External 1 - Configured to on board Broadcom LAN0 Wired to LAN0 Dlink1 1 - Configured to Intel port 1 LAN0 Wired to LAN0 Dlink1 1 - Configured to Intel port 2 LAN1 Wired to LAN1 Dlink2
As for the diagram a few people mentioned this is the quick down and dirty version. Nothing terribly complicated, and something I have done many times with VMware, but this client just refuses to let me implement vmware.