Attempting to make a site administrator user account for an Active Directory Domain. Using the Active Directory Delegate Authority Wizard. a user account has been grated rights in a OU. However, when attempting use of the authority some of the options are grayed out. Current settings allow the site admin to edit accounts created by the Site Admin, values are not grayed out. When the site admin attempts to edit user accounts created by Domain or Enterprise admin have some areas grayed out.
A user account that has all Authority of an administrator but limited to OU and it's children. Are desired.
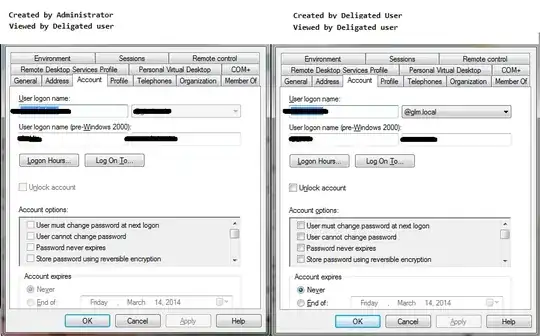
In the probmatic OU there are ~50 user objects 8 of those object inherit the pwdLastSet value. the Image on the right shows one of the objects that inherite the permissons. the left image shows a User object that has not. they are in the same OU.
In the Security tab for most the objects doe snot have my HelpDesk Group while the right image's Security tab does have the HelpdeskGroup with permissions.
for some reason the permissions are being inherated by some but not all the objects.
update
I tried with a different OU in a different forest with the same results
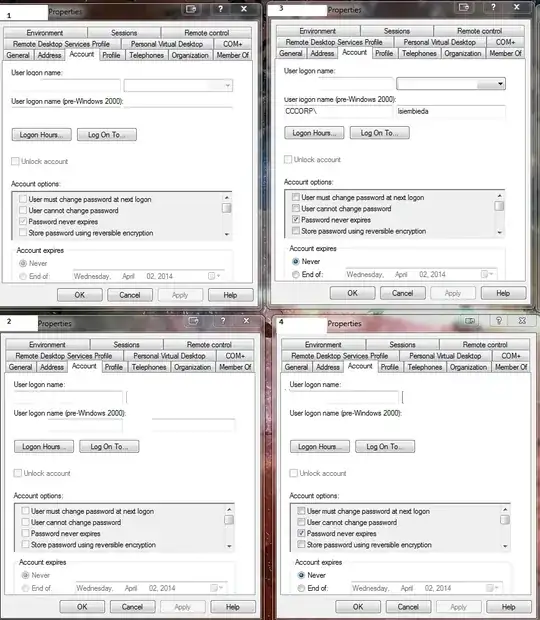
Step 1 make a new user account in forest
Step 2 right OU Delegate control
step 3 select my new user check all boxes
Using my new DelegatedAdmin account I navigate to the UO. There are 4 Users in the OU. Users 1&2 I am unable to edit. User 3&4 I am able to edit as expected.
Update
I have made a test OU with test users and a test administrator/helpdesk user. in these test OU's everything works exactly as it should. I fear there is something wrong with my Global catalog or Schema at this point.