From the Windows Mystery Caves:
a user trying to access a Windows Server 2008 R2 Remote Desktop Session Host is getting network timeouts upon connection establishment attempts. The Remote Desktop exception has been enabled and restricted (among other subnets) to the remote subnet 192.168.202.0/23. The user host's IP address is 192.168.203.63. The firewall log does not contain dropped connection attempt entries with this IP address.
If I change the Windows Firewall Logging settings for the domain profile and enable the logging of successful attempts like this,
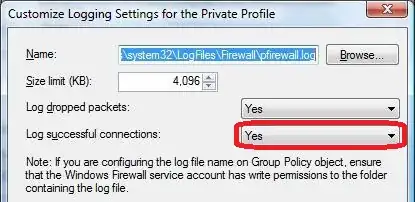
connections start to establish successfully and are logged with "ALLOW" entries in the firewall log. Disabling the logging of successful attempts breaks the user's connection establishment again. Another user's machine with a host IP address of 192.168.203.71 seems unaffected and can initiate connections even with logging disabled.
WTH? What exactly is the logging setting changing aside from actually enabling logging?