We have a number of situations where a client application needs to be migrated from one host to another in an active production network. The servers continue to run other applications.
The problem is that the remote application usually runs on an embedded system of some kind, and for reasons of risk avoidance, no changes are permitted to the configuration of these remote applications.
I can see that a router with (probably a fair amount) of NAT configuration can be made to transparently effect this change to force the traffic to another host on the network without touching the device. We might be able to convince some network level changes, but even these are not really welcome.
Firstly, is this the correct approach if the freezing cannot be avoided, and secondly, does anyone have any ideas (or even better a ready iptables ruleset) to implement something like this?
Edit
I was being intentionally non-specific, but this may help to clarify things. The client applications are typically embedded devices with proprietary TCP stream protocols. The constraint is specifically that we cannot change the device configuration, and would strongly prefer not to change the network or server configurations. This is both driven by risk from uncertainty and the availability of tools to manage the devices. There are many different types of devices with with a specific profile and this no single general solution.
This really requires some hardware interposed at the edge of the network to implement the redirection.
I realise that this can not exactly be considered good practice, but is something that we have inherited and have no control over. As we move forward, we will change the protocols to ones where the devices either are suitably configurable, or use devices that act as servers to avoid this problem.
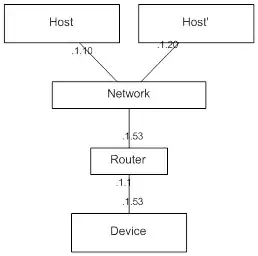
A diagram showing a typical required configuration is shown below.