The FTP config is actually looking into the FTP data to see the 530 code. You'll want to adapt the SSH config not the FTP config. Try this:
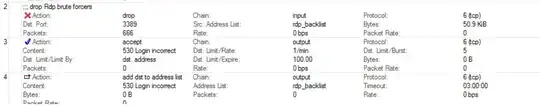
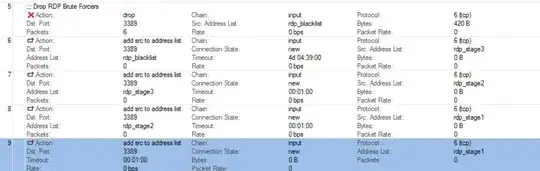
add chain=forward protocol=tcp dst-port=3389 src-address-list=rdp_blacklist action=drop \
comment="drop rdp brute forcers" disabled=no
add chain=forward protocol=tcp dst-port=3389 connection-state=new \
src-address-list=rdp_stage3 action=add-src-to-address-list address-list=rdp_blacklist \
address-list-timeout=10d comment="" disabled=no
add chain=forward protocol=tcp dst-port=3389 connection-state=new \
src-address-list=rdp_stage2 action=add-src-to-address-list address-list=rdp_stage3 \
address-list-timeout=1m comment="" disabled=no
add chain=forward protocol=tcp dst-port=3389 connection-state=new src-address-list=rdp_stage1 \
action=add-src-to-address-list address-list=rdp_stage2 address-list-timeout=1m comment="" disabled=no
add chain=forward protocol=tcp dst-port=3389 connection-state=new action=add-src-to-address-list \
address-list=rdp_stage1 address-list-timeout=1m comment="" disabled=no
What this config actually does, is for each incoming attempt it adds the IP address to a list. The first time it gets added to stage1, then if the IP is still in stage1 (after a minute) and another attempt is made, it gets added to stage2, and after it does this two more times it is added to the rdp_blacklist list where it actually gets blocked for 10 days.
If you want it to be more or less aggressive you can change the list timeouts, or even add more lists if you so desire.
You can add a list of these to allow specific IP ranges only:
add chain=forward dst-port=3389 src-address=192.168.0.0/24 action=accept
add chain=forward dst-port=3389 src-address=10.10.0.1/32 action=accept
add chain=forward dst-port=3389 action=drop
Just add as many of the src-address lines you need ahead of the final drop line.
If you have a LOT of ranges, you can create an address-list and reference that using this:
add chain=forward dst-port=3389 src-address-list=rdp_acceptlist action=accept
add chain=forward dst-port=3389 action=drop
And then add your addresses to the rdp_acceptlist
To add to the rdp_acceptlist use the following command:
/ip firewall address-list add list=rdp_acceptlist address=192.168.0.0/24