We have a requirement on our Watchguard Firebox XTM505 to be able to split our incoming external interface, in this case a fibre optic dedicated leased line, 100/100.
We use the line in our office of approx 30 machines however we also re-sell to an external company who utilise it to provide wireless internet solutions to the public.
The current infrastructure is as follows:
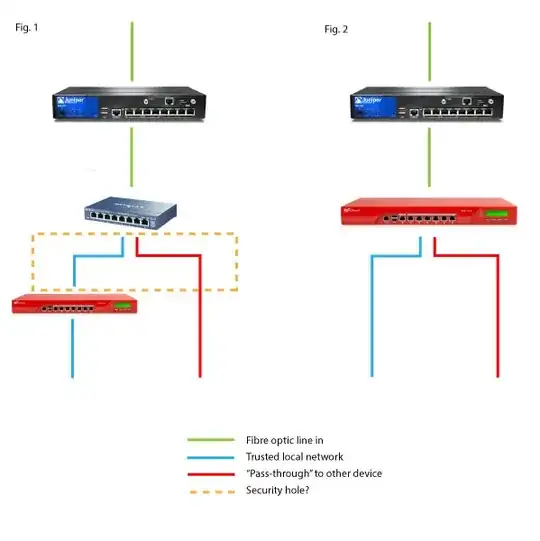
Data in (Leased Line) -> Juniper SRX210 managed by ISP -> 1 cable out into unmanaged Netgear switch -> 1 cable into our firewall and office network, 1 cable to our external providers core router managed by them.
We have been informed that having the unmanaged switch in the position it is poses a security risk and that a good option would be to get our Watchguard Firewall to perform the split, by separating our office onto a trusted interface, and by "passing through" the external line to their managed router. It is alleged that the Watchguard is capable of doing this and also rate limiting the interfaces, i.e. 20mbps for the trusted interface and 80mbps for the "pass-through", however Watchguard technical support don't seem to be able to understand what we're trying to achieve.
Can anyone provide any advice on whether this is possible on a Watchguard device and how or perhaps if there's a better way of achieving this, perhaps with a managed switch instead of unmanaged?
Edit: I have attached a diagram of what I'm trying to explain. So, fig.1 is what we have now and we've been informed that the orange dashed area is a security loophole. We want to separate the connections rather than just using a dumb switch, so fig.2 is something like what we want to achieve. However, the red line goes to another router controlled by a third party. We want to do as little as possible, ideally nothing to that side of the network as they handle all their routing and policies on their equipment, we're just trying to separate it before that. Of course if people think this is unnecesssary or there's a better way of achieving this then please do say!
Cheers