I have a vps, and have several site on it, usually these sites are rarely being visited except myself, thus i am shocked by one fact that is i visit the vps provider's portal and find i have used a huge amount of bandwidth that such a small site would never used.
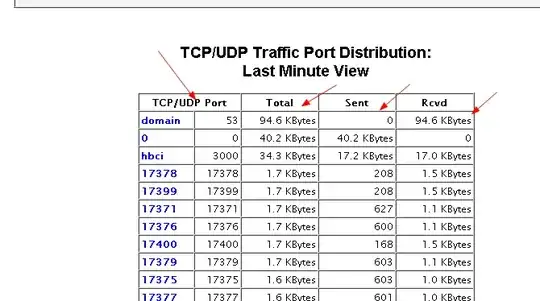
so i run ntop and reset all statistics then refresh the ntop web portal through 3000 port and find the diagram is really shocking, that DNS traffic occupies nearly 99 percent of all traffics, and the DNS traffic is nearly 100MB in several minutes, you could see this fact through the picture i uploaded
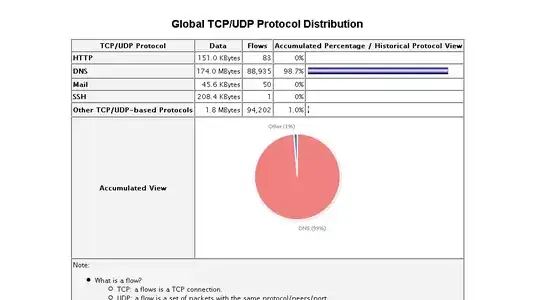
My Question is as follows: 1. Why there is so huge DNS traffic on my VPS? 2. Is my VPS hacked by someone that my VPS is configured as a core of dns traffic?
Edit 1 @RSchulze why you said the reason is because of mis configuration of dns software such as named? which kind of mis configuration could result in such huge dns traffic? btw, i don't configure named manually, i configure it using kloxo, which is a Host management software and it's author just sucided for hack attack against kloxo:( i still think my server maybe hacked:( maybe i should learn wireshark and capture some packages in order to know the origin and target of this DNS traffic
Edit 2 After i kill the named process, there is seldom DNS traffic now:) but why there is still some DNS related traffic, but they are all received traffic, no send traffic:) does that mean my VPS send some DNS request to other hosts?