We have a huge trouble :( .. Our mac server makes a spam delivery. Our IP already blacklisted in about a dozen of servers (checked with http://mxtoolbox.com/). We have another computers in the same networks, including PC. What I already did and discovered:
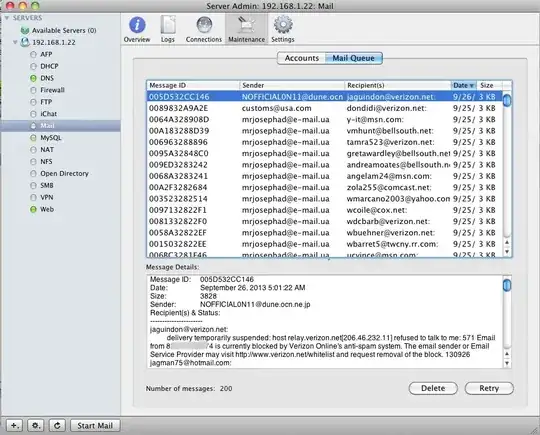
- I found a spam emails in the "Server Admin app"->Mail->Maintenance->Mail Queue (attached image).
- I managed to get one of those emails from /var/spool/postfix/ folder. Here is the link - simple HTML file (http://www.sendspace.com/file/wbyjov).
- I searched for malware with ClamXav on the server - with no help
- I re-checked PC computers with antivirus - with no help
Also, the fact that these emails appears in "Mail Queue" means that Mac OS server sends them by itself, right? Or is it possible that another computer in the same network sends them?
Thank you in advance for you answers!!!!
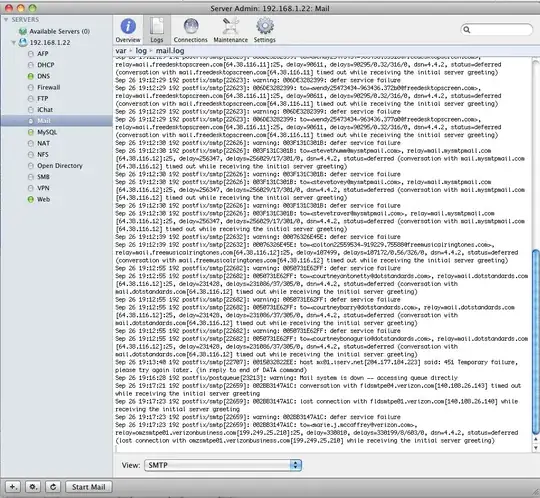
* Added two screenshots of server Logs: SMTP logs and IMAP logs *
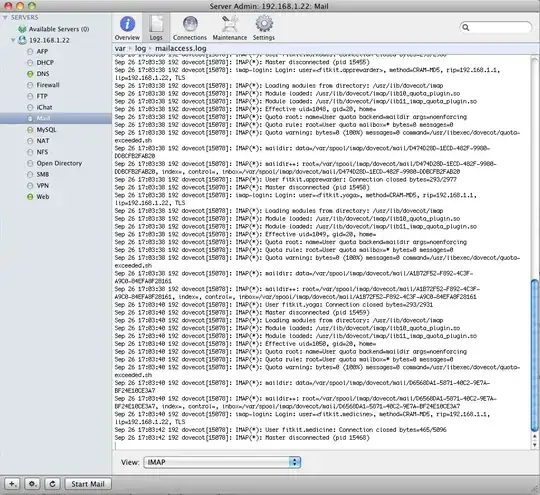
* Added a screenshot of Access logs. I know for sure that "fitkit.medicine" account shouldn't be used at this time at all. Does it means that some malware hacked several accounts on the server? *