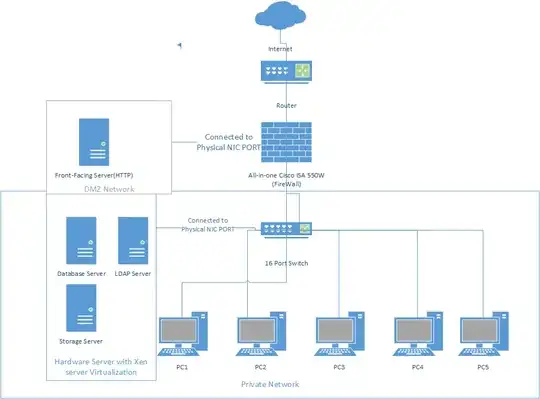
I have the following proposed network design that I will be implementing.
- All connection for server and PCs are connected through an All in One cisco firewall
- Only one high end server will be used. The server has two NICs.
Virtualization will be used DMZ0network port connected to the server from the firewall.
(The virtualized http server will use this port)- The PCs are connected to a switch that is from the firewall, this network is private
- The server will have another NIC port connected to the switch, the server that is not exposed to the DMZ network, will use this.
Questions:
- I've been playing which virtualised software for this setup, will Xen Cloud platform work for this diagram?
- Will this physical separation of network using two NICs work for the server?
Will it work with the Xen Cloud platform? - Are there other problems that I may face from this setup?