We received an email last year from our hosting provider regarding one of our accounts- it had been compromised and used to deliver a rather generous helping of spam.
Apparently, the user had reset her password to a variation of her name (last name is something you could probably guess first time.) She promptly got hacked within a week- her account sent out a deluge of 270,000 spam emails- and was very quickly blocked.
So far, nothing particularly unusual. That happens. You change your passwords to something more secure, educate the user and move on.
However, something concerned me even more than the fact one of our accounts had been compromised.
Our hosting provider, in an effort to be helpful, actually quoted the password to us in the following email:
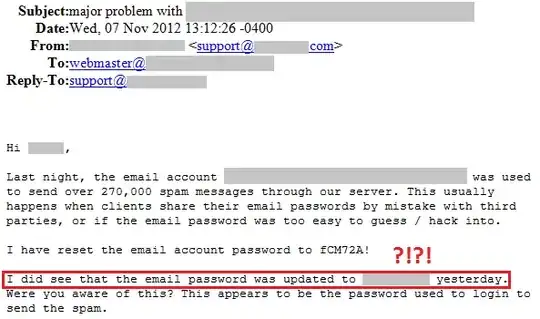
I am astonished. We are due to renew our contract soon- and this feels like a dealbreaker.
How common is it for a hosting provider to be able to find out the actual password used on an account?
Do most hosting providers have an account abuse department that has more access than front-line reps (and can look up passwords if necessary), or are these guys just not following best-practice in making it possible for any of their staff to access user passwords? I thought passwords were supposed to be hashed and not retrievable? Does this mean they store everyone's passwords in plain text?
Is it even legal for a hosting provider to be able to discover account passwords in this fashion? It just seems so incredible to me.
Before we look into changing provider, I would like some reassurance that this is not common practice, and that our next hosting provider wouldn't also likely have things set up the same way.
Looking forward to hearing your views on this.